A Comprehensive Guide to OAuth 2.0: Grant Types, Security, and Implementation
Mastering the OAuth 2.0 grant types enables developers to design secure and user-friendly authorization workflows for their applications.
OAuth is a widely adopted authorization framework that allows third-party applications to access user resources without exposing user credentials. This protocol has evolved significantly through its versions, with OAuth 2.0 being the current standard that enhances security, flexibility, and usability compared to its predecessor, OAuth 1.0.
What is OAuth 2.0?
OAuth 2.0 is an industry-standard authorization protocol that facilitates secure delegated access between applications (clients) and user accounts hosted on separate services (resource servers). This mechanism enables users to grant applications limited access to their resources while keeping their credentials confidential.

OAuth 2.0 Grant Types
The OAuth 2.0 framework defines several methods by which clients can obtain access tokens from the authorization server to access user resources on the resource server. This guide provides a detailed exploration of the most common OAuth 2.0 grant types, including Authorization Code, Resource Owner Password Credentials, Client Credentials, Implicit, and Refresh Tokens.
Overview of Common OAuth 2.0 Grant Types
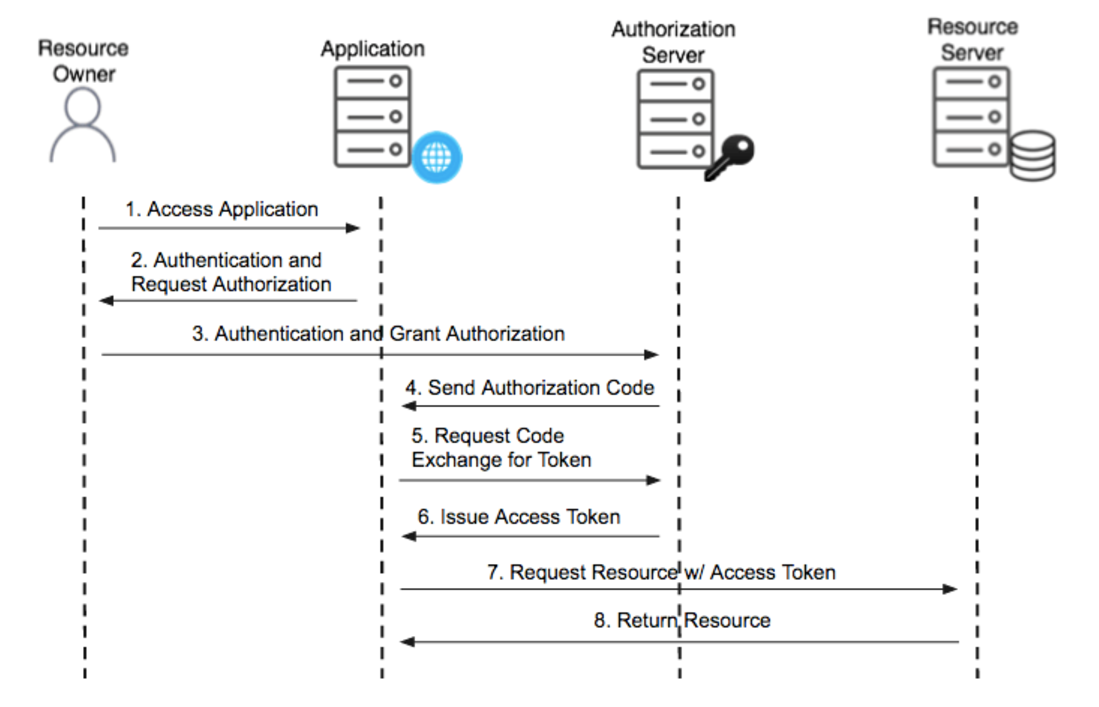
1. Authorization Code Grant:
This flow is widely used for its robust security.
- Steps:
- The user consents to the client accessing their resources.
- The authorization server returns a temporary authorization code to the client.
- The client exchanges this code for an access token from the authorization server.
- The access token is used by the client to access user resources on the resource server.
- Pros: High security as authorization codes and access tokens are separate; ideal for server-side applications that can securely store client secrets.
- Cons: Involves multiple redirects between the client, authorization server, and resource server.
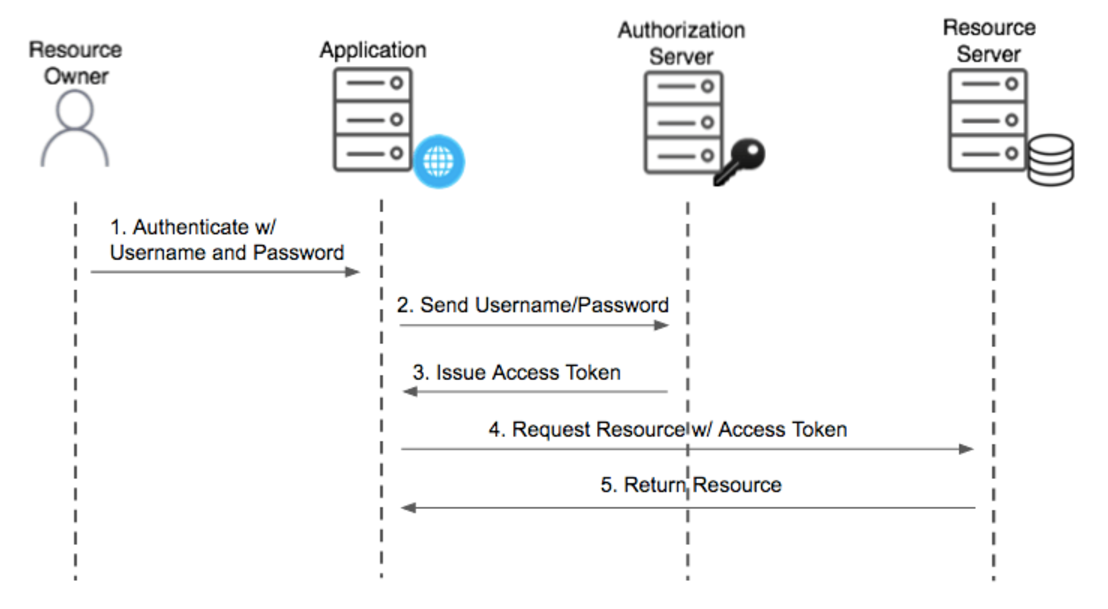
2. Resource Owner Password Credentials Grant:
This method directly uses user credentials (username and password).
- Steps:
- The client collects the user's credentials.
- These credentials are sent to the authorization server for verification and token exchange.
- Upon successful verification, the client receives an access token.
- Pros: Simple implementation, suitable for trusted first-party applications.
- Cons: Lower security due to direct exposure of user credentials; not recommended for public clients.
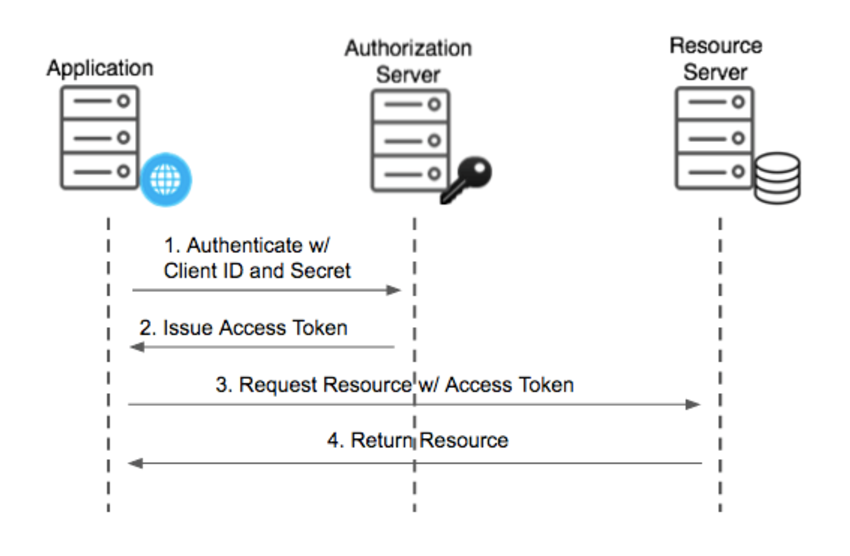
3. Client Credentials Grant:
This grant is specifically for scenarios where applications act on their behalf rather than on behalf of a user.
- Steps:
The client requests an access token from the authorization server using its unique identifier and secret. - Pros: Effective for machine-to-machine interactions that do not require user involvement.
- Cons: Access permissions are granted to the application itself, requiring careful consideration of the permissions allowed.
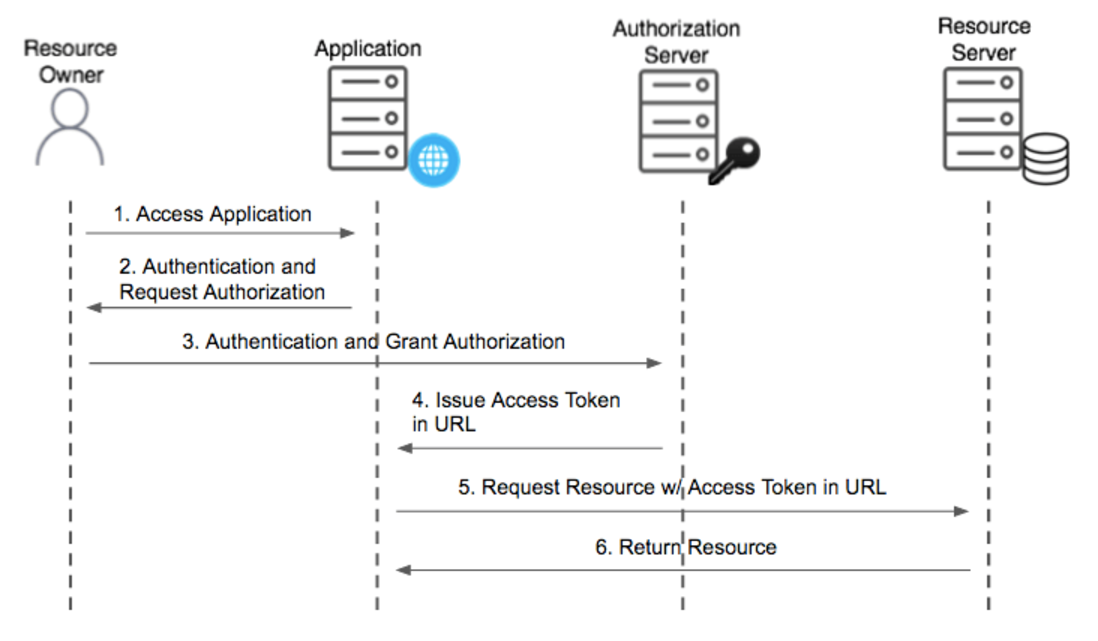
4. Implicit Grant:
This flow simplifies the process for mobile or single-page applications by returning the access token directly to the client.
- Pros: Streamlined user experience due to single redirect.
- Cons: Lower security since access tokens are exposed to the client; not recommended for sensitive data.
- Refresh Token Grant:
This provides a mechanism to obtain a new access token without re-authenticating the user when the original access token expires.- Steps:
The client uses the refresh token obtained during the initial authorization process to request a new access token from the authorization server. - Pros: Enhances user experience by reducing the frequency of login prompts.
- Cons: Introduces another token that requires secure management.
- Steps:
Choosing the Right OAuth 2.0 Grant Type for Your API
When selecting the appropriate OAuth 2.0 grant type for your API, consider the following factors:
- Security Requirements:
- High Security Needed: Choose the Authorization Code Grant to minimize risk by keeping authorization codes and tokens separate.
- Lower Security Concerns: If you have a trusted client application, the Resource Owner Password Credentials Grant may suffice, but handle with caution due to exposed credentials.
- User Experience:
- Seamless Experience Required: Implicit Grant can be quick but involves security trade-offs.
- Balance Convenience and Security: Authorization Code Grant offers a good compromise, despite the additional redirects involved.
- Type of Client Application:
- Secure Server-Side Storage (Web Applications): Both Authorization Code Grant and Client Credentials Grant are viable options.
- Public Client Applications (Mobile Apps): Implement Authorization Code Grant with PKCE (Proof Key for Code Exchange) to improve security.
- Machine-to-Machine Communication: Client Credentials Grant is the preferred method.
Using EchoAPI for OAuth 2.0 Authentication
EchoAPI is a comprehensive API development platform that simplifies building, testing, and documenting APIs. With its features, developers can seamlessly manage OAuth 2.0 authentication during the entire API lifecycle.
Building an API with EchoAPI
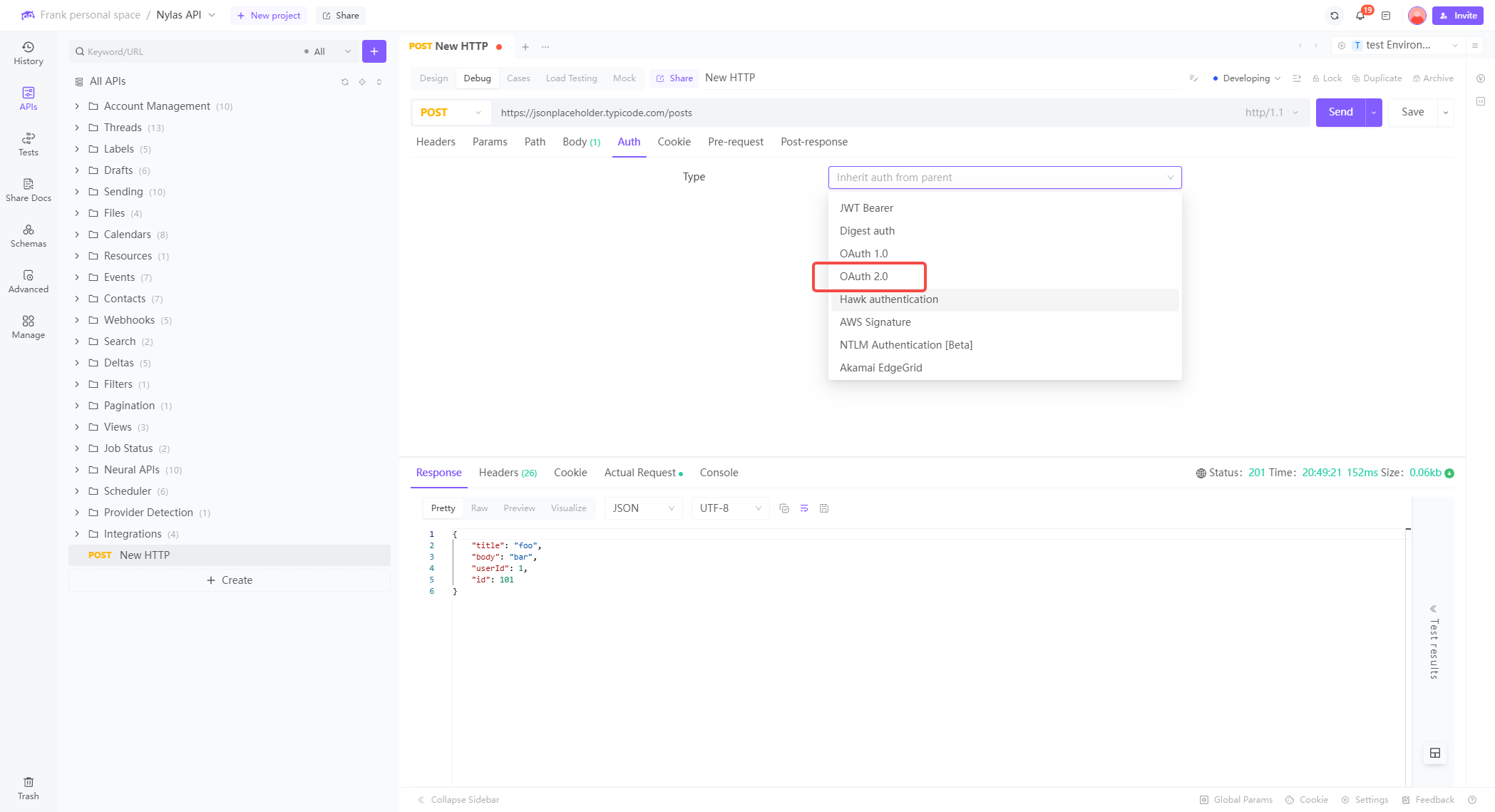
To create an API from scratch using EchoAPI, follow these steps:
- Click the New HTTP button.
- Choose various API features, such as:
- HTTP methods (GET, POST, PUT, DELETE)
- API endpoint URL for client-server interaction
- Parameters to be passed in the API URL
- Description of the API’s intended functionality
For best practices in creating REST APIs, consider reading resources on API development.
Selecting OAuth 2.0 Authentication in EchoAPI
With EchoAPI's user-friendly interface, you can easily select OAuth 2.0 authentication in seconds:
- After creating a new request, select OAuth 2.0 as the authentication type.
- This selection ensures your API benefits from enhanced security measures.
Conclusion
Mastering the OAuth 2.0 grant types enables developers to design secure and user-friendly authorization workflows for their applications. By carefully evaluating security implications, user experience, and application types, developers can choose the most suitable grant type, ensuring a balance between robust access control and seamless user interactions.
Understanding the nuances of OAuth 2.0 is essential for developers seeking to implement secure and efficient authorization mechanisms in their applications. Utilizing the knowledge and tools provided can facilitate informed decision-making and enhance the overall security of user data.
Key Takeaways
- Always prioritize security when handling sensitive data.
- Understand the implications of each OAuth grant type.
- Use tools like EchoAPI to streamline the implementation and management of OAuth 2.0 authentication.
By following these guidelines, you will be better equipped to implement robust OAuth 2.0 solutions for your applications.




 EchoAPI for VS Code
EchoAPI for VS Code

 EchoAPI for IntelliJ IDEA
EchoAPI for IntelliJ IDEA

 EchoAPl-Interceptor
EchoAPl-Interceptor

 EchoAPl CLI
EchoAPl CLI
 EchoAPI Client
EchoAPI Client API Design
API Design
 API Debug
API Debug
 API Documentation
API Documentation
 Mock Server
Mock Server








