Basic Auth vs. Bearer Token: Choosing the Best Authentication Method for Your API
Choosing the right API authentication is crucial. We explain Basic Auth vs. Bearer Token and guide your choice.
Choosing the right authentication method for your API is crucial. Two popular options are Basic Authentication (Basic Auth) and Bearer Token. This post breaks down their differences, pros and cons, and guides you on which one to use for your API needs.

What Is Basic Authentication?
Let’s start with Basic Auth. Imagine you’re at a club’s entrance, and the bouncer asks for your ID. You show it, and if everything checks out, you’re allowed in. Basic Auth works similarly. It’s one of the simplest forms of authentication, where a user provides a username and password, which is then encoded in Base64.
How Does Basic Auth Work?
- Client Request: When a client wants to access an API endpoint, it sends a request with an authorization header.
- Authorization Header: This header contains the word "Basic" followed by a space and then the Base64-encoded username and password.
- Server Validation: The server decodes this string, checks the credentials, and grants access if everything is correct.
Example of an Authorization header:
Authorization: Basic dXNlcm5hbWU6cGFzc3dvcmQ=
In this example, dXNlcm5hbWU6cGFzc3dvcmQ= is the Base64-encoded string of the username and password combination.
Pros of Using Basic Auth
- Simplicity: Easy to implement without the need for complex setups.
- Widely Supported: Supported by almost all HTTP clients and servers.
- No Dependency: Doesn’t require external libraries or tokens, making it lightweight.
Cons of Using Basic Auth
- Security Risks: Credentials are sent with every request and are only Base64-encoded, not encrypted.
- No Session Management: Each request includes credentials, which can be inefficient and insecure.
- Limited Scalability: Not suitable for complex systems needing different user permissions or sessions.
What Is a Bearer Token?
Now, let’s move on to Bearer Tokens. Think of a Bearer Token like a VIP pass at a concert. Once you have it, you don’t need to show your ID every time you enter a restricted area. The token itself is proof that you have access.
How Does Bearer Token Work?
- Token Issuance: When a user logs in successfully, the server generates a token, usually a JSON Web Token (JWT).
- Token Storage: This token is stored on the client side, either in local storage, a cookie, or elsewhere.
- Authorization Header: For subsequent API requests, the client includes this token in the Authorization header.
- Server Validation: The server checks the token’s validity and grants access if the token is valid and unexpired.
Example of an Authorization header with a Bearer Token:
Authorization: Bearer eyJhbGciOiJIUzI1NiIsInR5cCI6IkpXVCJ9...
The token is a long, encoded string carrying encoded information, like the user ID and expiration time.
Pros of Using Bearer Token
- Enhanced Security: Usually time-limited and can be encrypted, offers better security than Basic Auth.
- Statelessness: The server doesn’t need to store session data, just validates the token on each request.
- Flexibility: Can include different scopes or permissions, making them versatile for complex APIs.
Cons of Using Bearer Token
- Implementation Complexity: More involved setup compared to Basic Auth, requiring token generation, storage, and validation.
- Token Management: Tokens need to be securely stored and refreshed when they expire, adding complexity to client-side management.
- Overhead: For smaller APIs or internal tools, the additional security might be overkill and introduce unnecessary overhead.
Side-by-Side Comparison
| Feature | Basic Auth | Bearer Token |
|---|---|---|
| Security | Low (credentials sent with every request) | High (tokens can be encrypted and time-limited) |
| Ease of Implementation | Very Easy | Moderate to Complex |
| Session Management | None | Stateless |
| Performance | Can be slower due to credentials sent with each request | Generally faster with token-based access |
| Scalability | Limited | Highly Scalable |
When to Use Basic Auth
Basic Auth might be the right choice if:
- You’re working on a small, internal API with minimal security concerns.
- You need a quick and straightforward authentication method.
- The API usage is low and doesn’t require session management or complex permissions.
When to Use Bearer Token
Bearer Token is ideal if:
- Security is a top priority for your API, especially if it’s public-facing.
- Your API handles sensitive data or requires complex user permissions.
- You need a scalable solution that can manage different user roles and scopes.
Transitioning from Basic Auth to Bearer Token
If you’re currently using Basic Auth and considering a move to Bearer Token, here’s how you can make the transition smoother:
- Evaluate Your Needs: Determine why you need to switch. Are you scaling up? Do you need better security?
- Token Generation: Implement a system to generate and manage tokens. JWT is a popular choice.
- Client-Side Adjustments: Update your clients to store and use tokens instead of sending credentials with each request.
- Server-Side Validation: Ensure your server can decode and validate the tokens. You might need to adjust your authentication middleware.
- Gradual Rollout: Consider rolling out the new system gradually to allow time for testing and fixing issues. You can run both authentication methods concurrently initially and eventually phase out Basic Auth.
Security Considerations: How Safe Are They?
Basic Auth Security
Basic Auth’s biggest security flaw is sending the user’s credentials with every request. Although Base64-encoded, it’s not encrypted. Always use HTTPS to ensure credentials are encrypted during transmission, but remember, if HTTPS is compromised, the credentials are still vulnerable.
Bearer Token Security
Bearer Token offers better security through:
- Token Encryption: Harder to decode if intercepted.
- Time-Limited: Reducing risk if a token is compromised.
- Scoping: Includes scopes that limit actions even if a token is stolen.
However, a stolen and unexpired token can still access the API. Implement additional security measures, like token refresh and invalidation strategies.
API Use Cases: Real-World Examples
- Internal Company API: An internal API for a small company might use Basic Auth because it’s easy to set up with minimal security risks.
- Public API for a Banking App: A public-facing API for a banking app would benefit from Bearer Token authentication due to enhanced security and scalability.
- Third-Party Integrations: For APIs involving third-party integrations, Bearer Token is preferred for temporary access to specific resources without exposing main credentials.
EchoAPI: Your Reliable Partner in API Management
EchoAPI is an innovative platform designed to make managing and securing your APIs seamless. Offering a variety of authentication methods, EchoAPI has your back, whether you prefer Basic Authentication, Bearer Tokens, or advanced features like OAuth and JWT.
Why Choose EchoAPI?
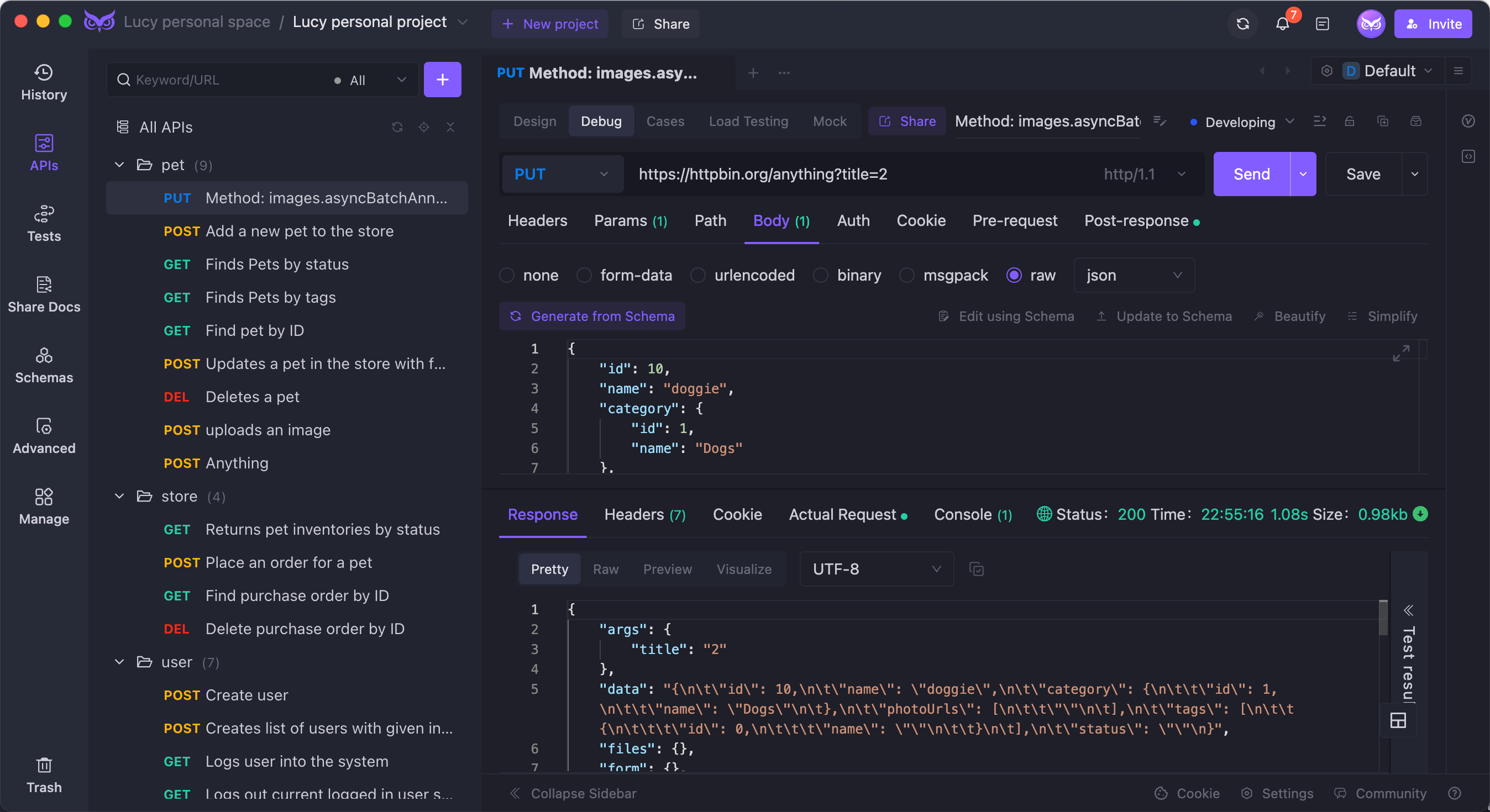
EchoAPI is the rockstar alternative to Postman, designed as an ultra-lightweight, no-login-required tool for API design, debugging, automated testing, and load testing. It supports Scratch Pad for quick notes and works perfectly with Postman script syntax. EchoAPI also comes with plugins for IntelliJ IDEA, VS Code, and a Chrome request capture extension.
EchoAPI Extensions and Tools
Besides the desktop application, EchoAPI offers several extensions to fit various development environments:
- EchoAPI for VS Code
- Ultra-lightweight API debugging tool for VS Code.
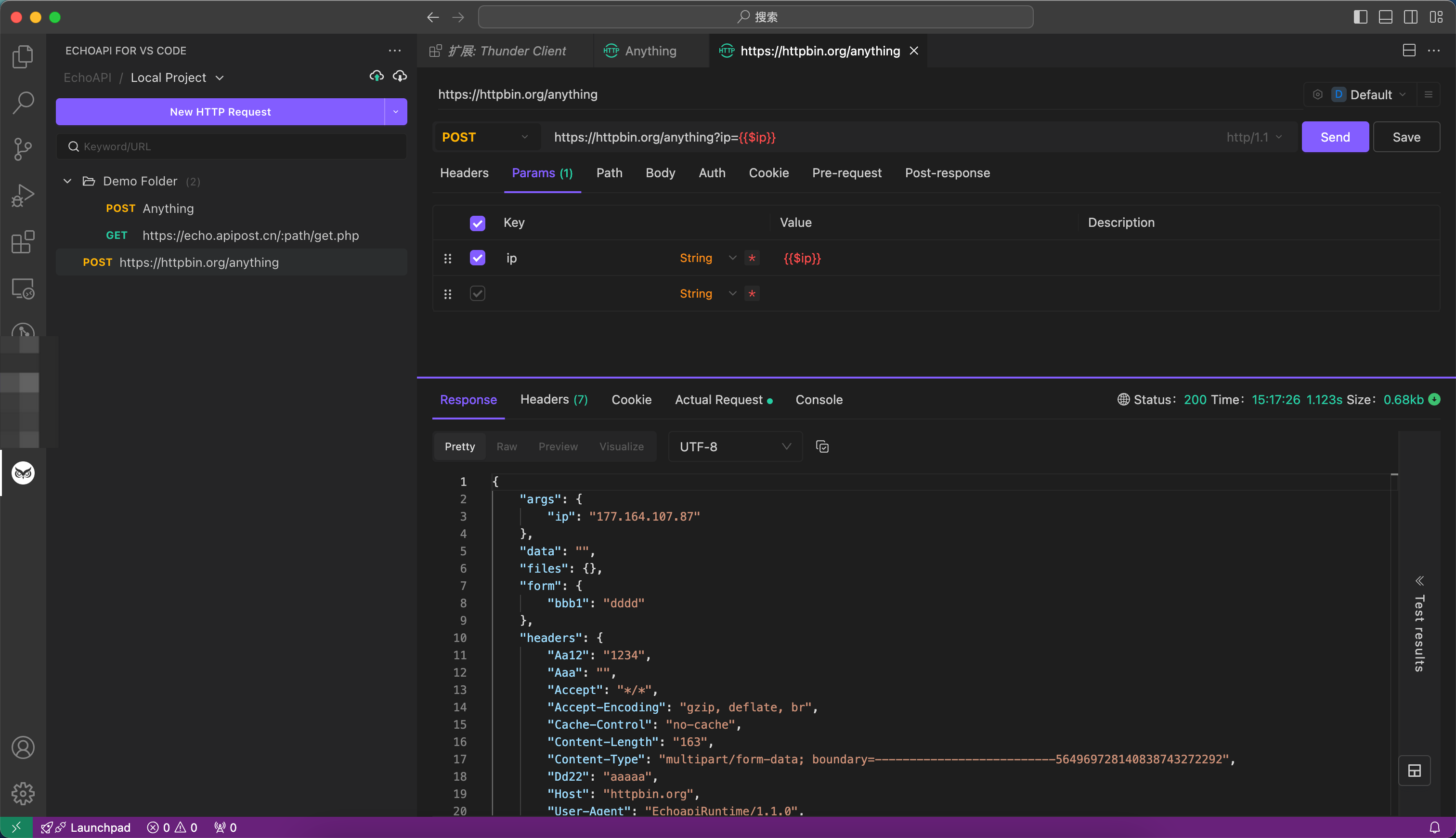
- EchoAPI for IntelliJ IDEA
- One-click API documentation, one-click debugging.
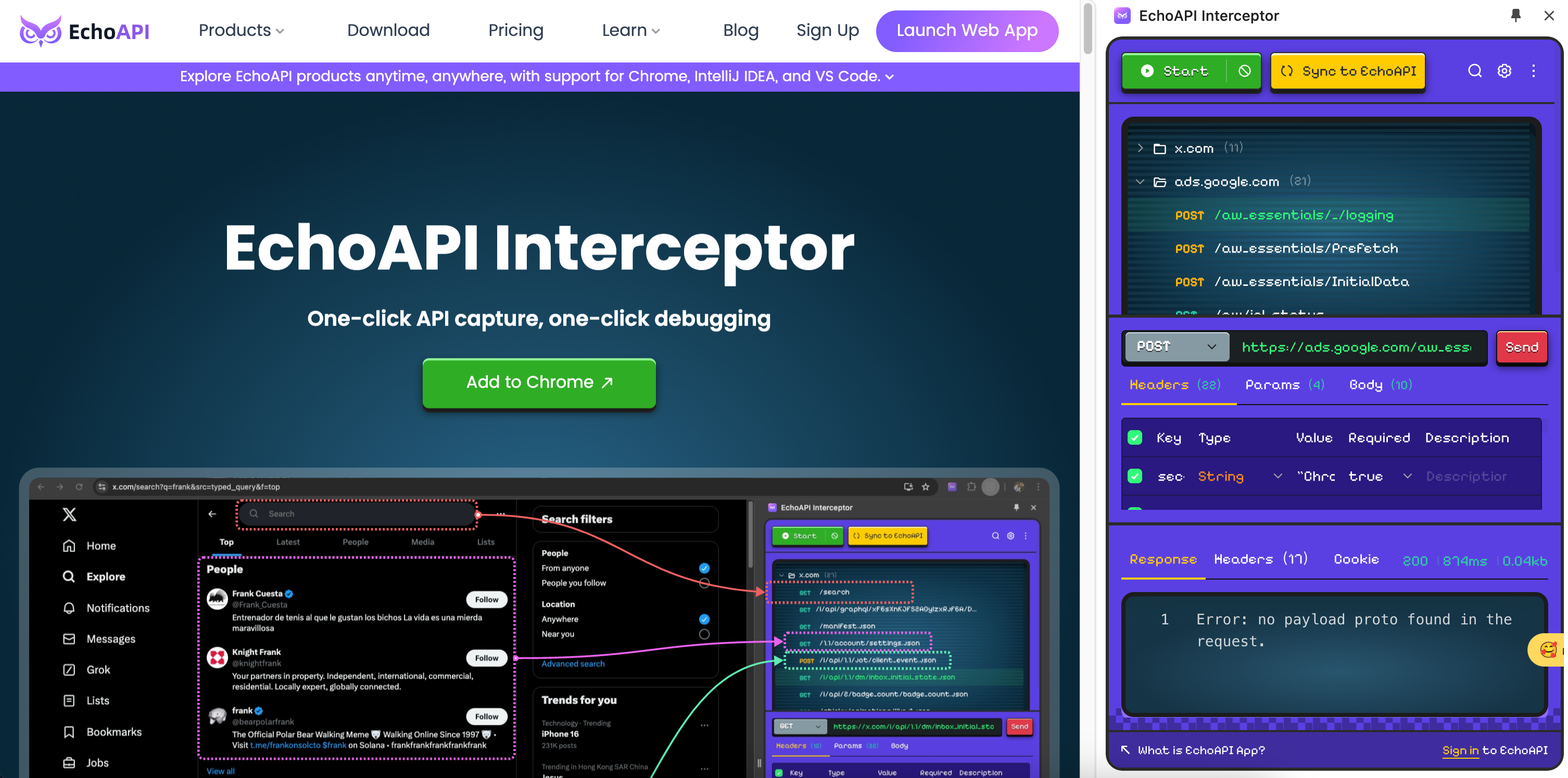
- EchoAPI-Interceptor
- One-click API capture, one-click debugging.
- EchoAPI CLI
- Command Line Interface tool for EchoAPI and test case execution.
These tools make it easy for developers to choose the best option for their workflow.
Key Features of EchoAPI:
- No Login Required: Jump in and start working without creating an account.
- Supports Scratch Pad: Handy for jotting down ideas or quick tests.
- Ultra Lightweight: Fast and doesn't weigh down your system.
- 100% Postman Script Compatibility: Easily switch from Postman without rewriting your scripts.
EchoAPI also supports other methods like Bearer Tokens, OAuth, and JWT—configure the appropriate settings for your chosen method.
Best Practices for Implementing API Authentication
- Always Use HTTPS: Ensures data is encrypted during transmission.
- Implement Rate Limiting: Protects your API from abuse by limiting requests.
- Regularly Rotate Tokens: Minimizes risk of token misuse.
- Audit and Monitor: Detects suspicious activity early.
- Educate Users: Guide on secure storage and management of credentials or tokens.
Conclusion: Choosing the Right Authentication for Your API
Deciding between Basic Auth and Bearer Token depends on your specific needs. Basic Auth offers simplicity but comes with significant security risks. Bearer Token, while more complex, provides enhanced security, scalability, and flexibility.
Managing APIs regularly? EchoAPI is a powerful tool that simplifies your workflow and ensures your API is secure and efficient, whether using Basic Auth or Bearer Token.




 EchoAPI for VS Code
EchoAPI for VS Code

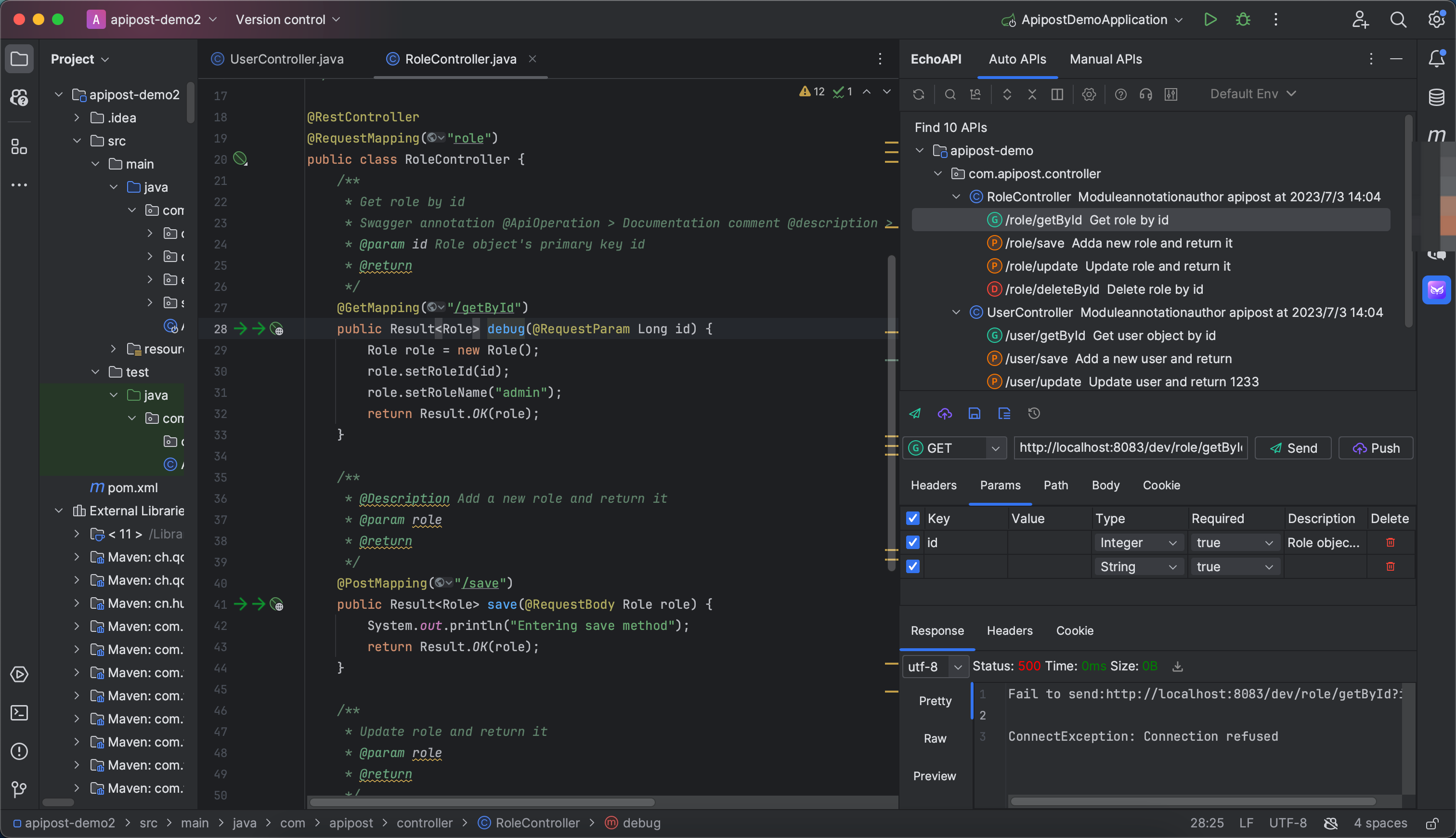
 EchoAPI for IntelliJ IDEA
EchoAPI for IntelliJ IDEA

 EchoAPl-Interceptor
EchoAPl-Interceptor

 EchoAPl CLI
EchoAPl CLI
 EchoAPI Client
EchoAPI Client API Design
API Design
 API Debug
API Debug
 API Documentation
API Documentation
 Mock Server
Mock Server








