Mastering Postman: Cookie and Token Authentication
In this article, we will dive deep into the realms of Cookie Authentication and Token Authentication, two pivotal security strategies.
In the realm of web services and API management, understanding the core mechanisms that secure the communication between the client and server is crucial. In this article, we will dive deep into the realms of Cookie Authentication and Token Authentication, two pivotal security strategies. Our journey will include practical examples using Postman and echoAPI Interceptor, highlighting their implementation and nuances.
What Are Cookies?
A cookie is a small piece of text stored on the client's machine that is used primarily for session management, user personalization, and tracking user behavior. In a key=value format, cookies operate serving as tiny data keepers.

How Cookie Authentication Works
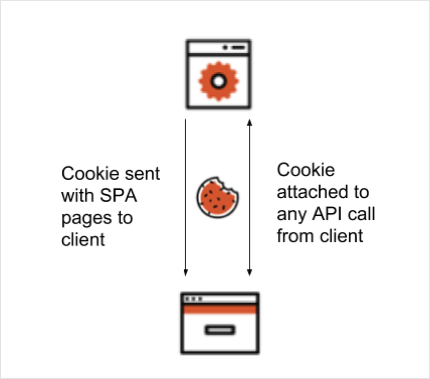
Cookie authentication is a server-side method of maintaining state between HTTP transactions. It works as follows:
- Initial Request by Client: During the first visit to a server, if authentication is needed, the server generates a cookie.
- Cookie in Response Header: This cookie is sent back with the response, embedded in the
Set-Cookieheader. - Subsequent Requests: On subsequent requests, the client returns this cookie to the server in the
Cookieheader, allowing the server to validate the session.
Types of Cookies:
- Session Cookies: Stored in memory and deleted when the browser is closed.
- Persistent Cookies: Stored on the hard drive until they expire (as defined by their expiration date) or until the user deletes the cookie.
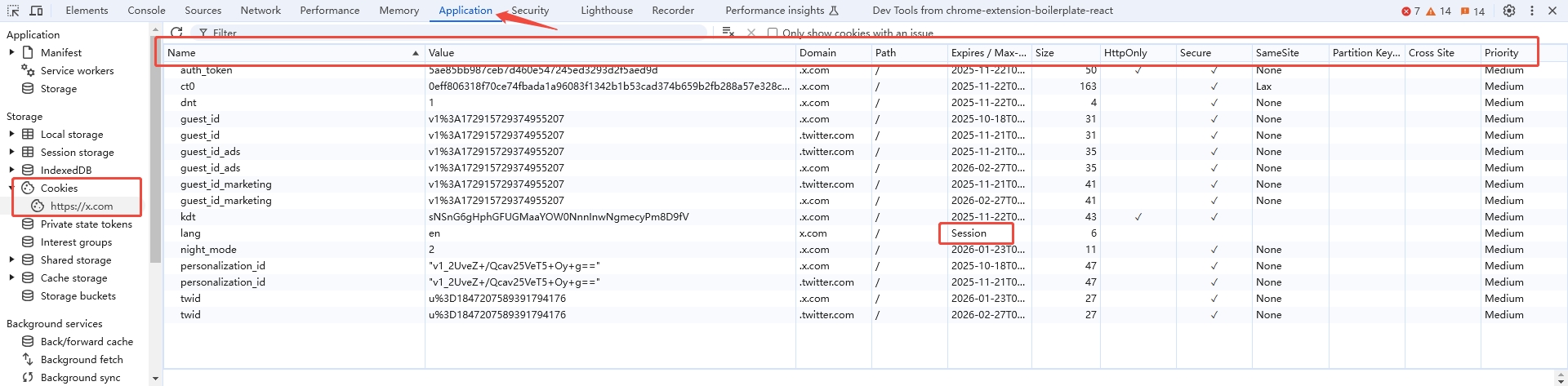
To inspect cookies, one can use the browser's Developer Tools under the Application panel to see details such as Name, Value, Domain, Path, and Expires/Max-Age.
Practical Example: Debugging API Authentication
Let us detail the steps to understand cookie and token authentication via practical debugging:
Tools Used:
- EchoAPI Interceptor: A modern tool for capturing and inspecting HTTP traffic.
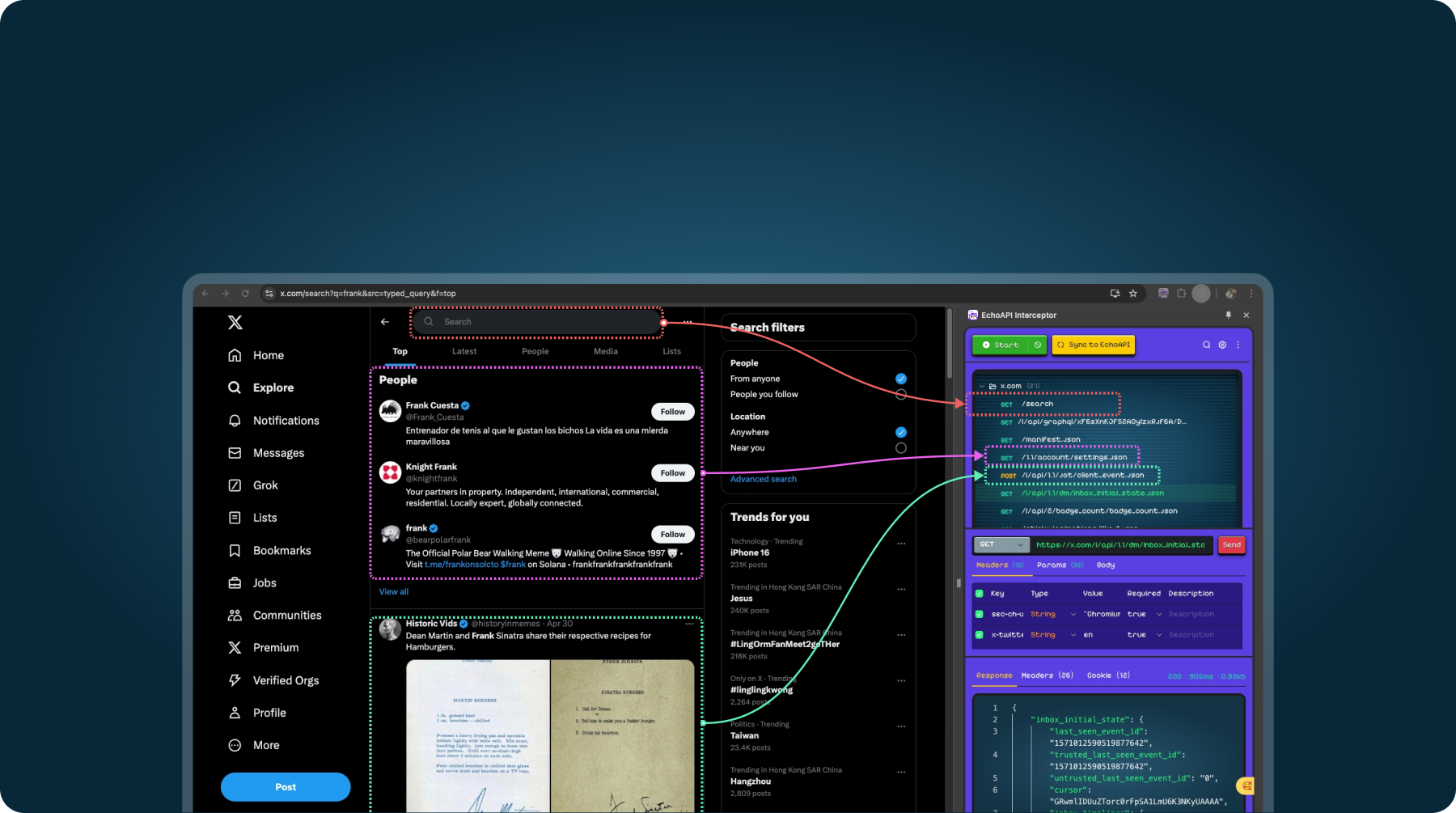

Steps in Action:
1. Setup:
Post login, echoAPI Interceptor automatically captures the traffic including URLs, parameters, and cookies of the session.
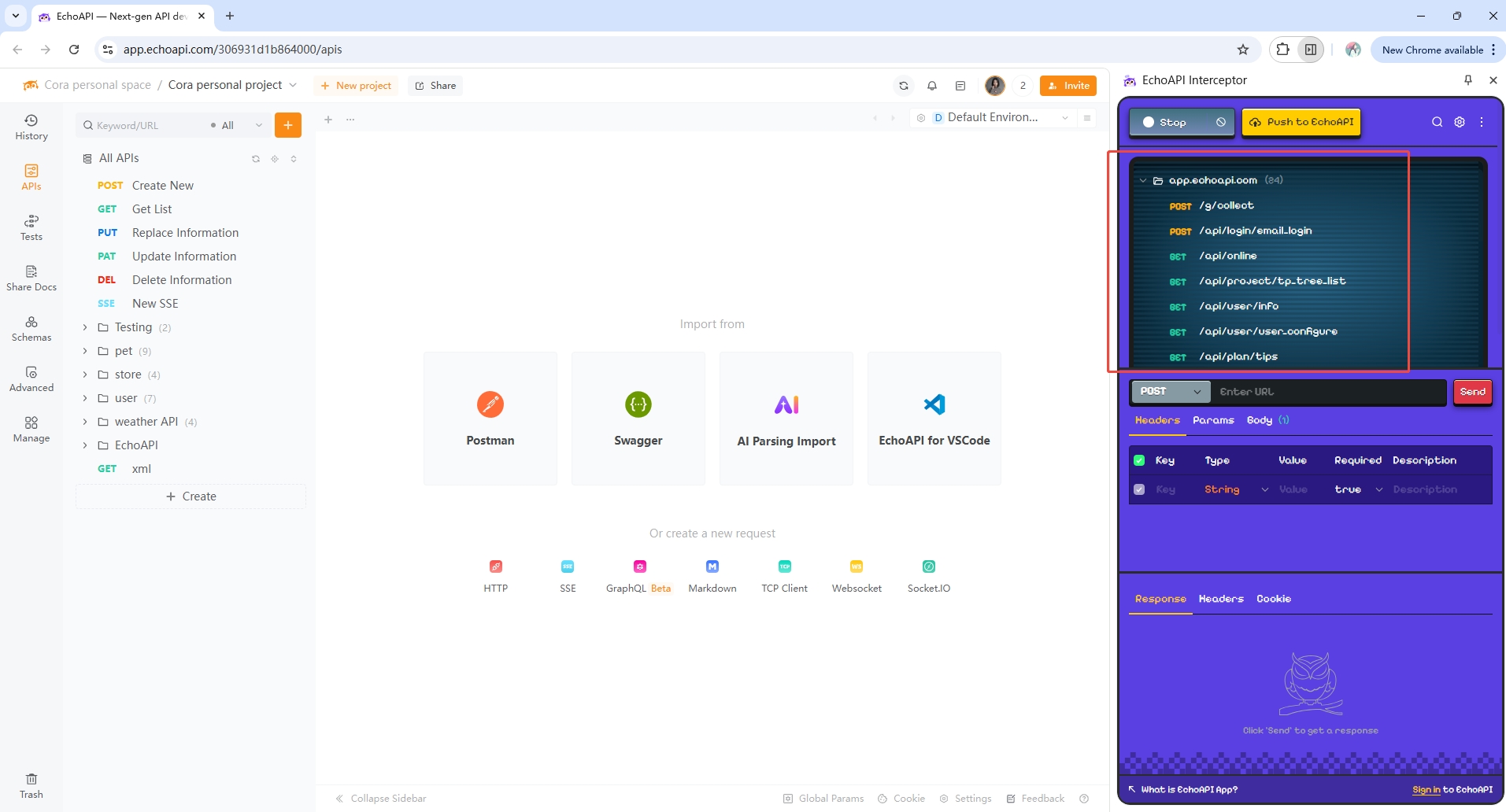
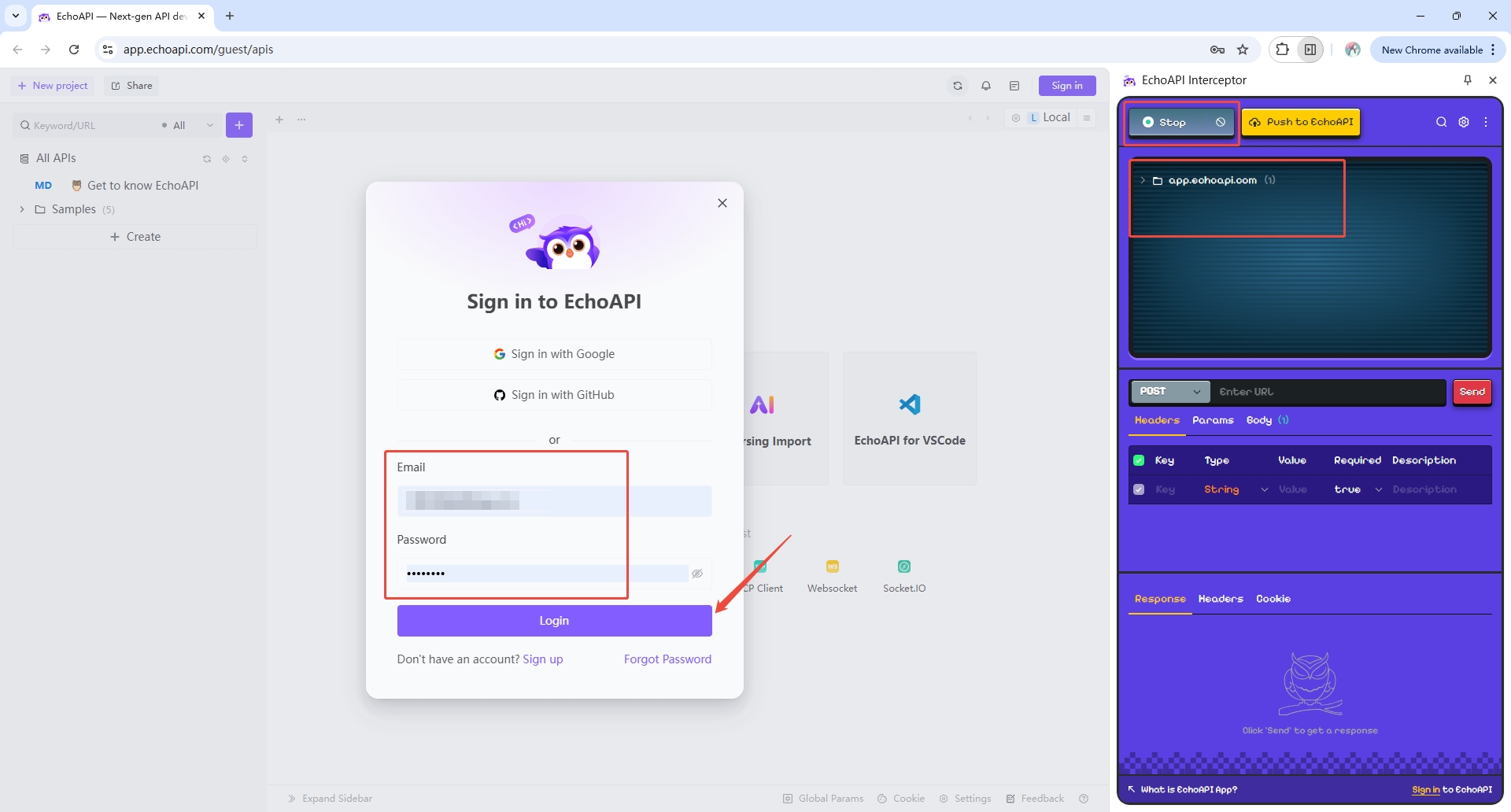
Navigate to the login page at https://app.echoapi.com/login and perform the login with credentials.
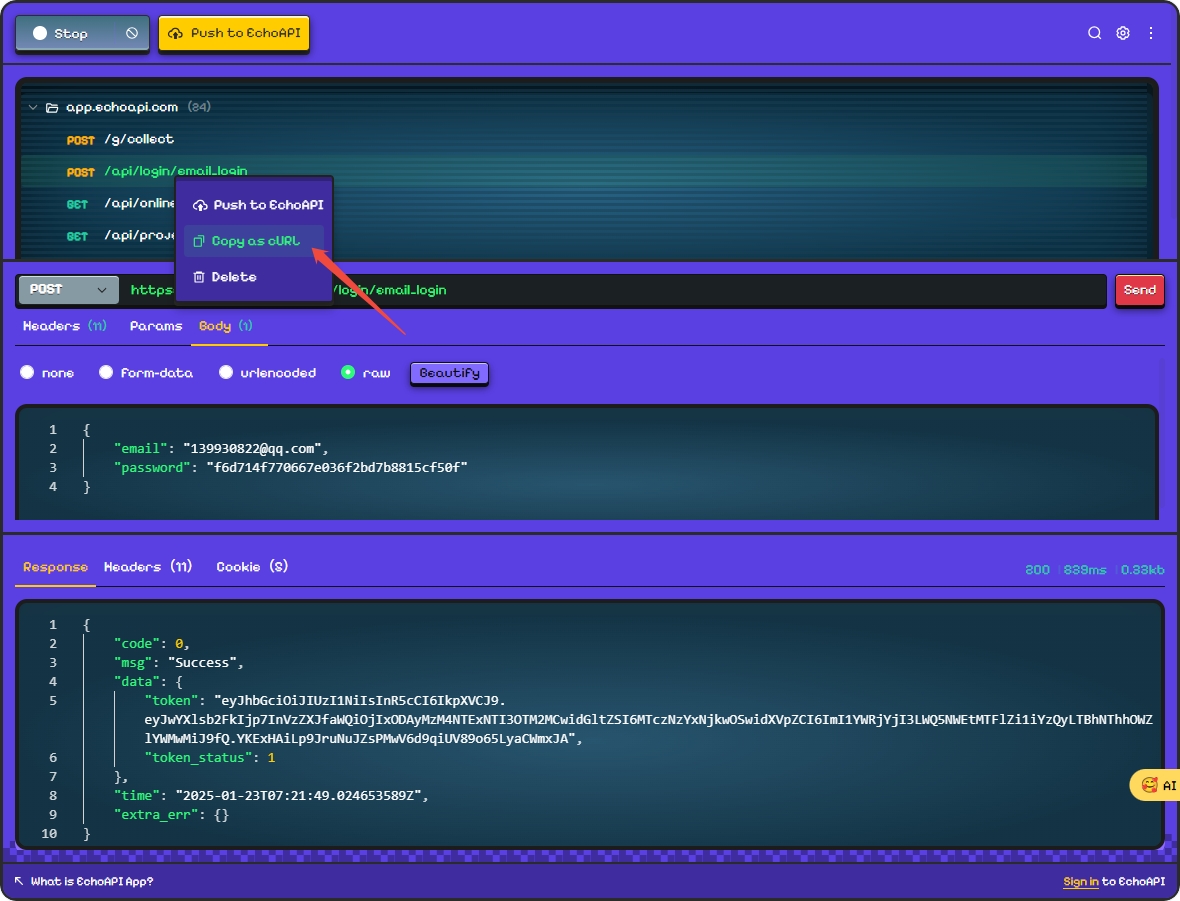
2. Copying curl for API:
Right-click the API and choose to copy as curl.
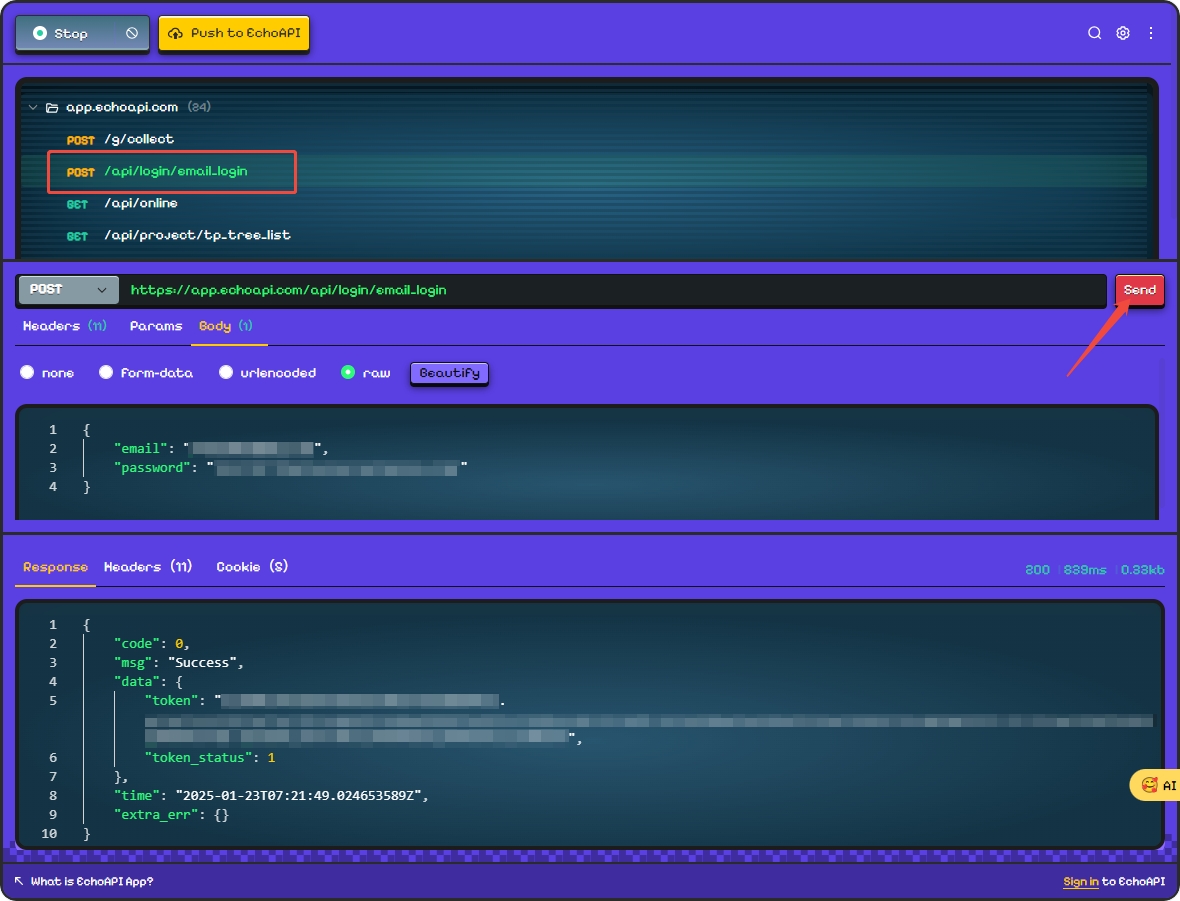
Click on the login API from the captured list, send the request, and ensure it is debuggable.
3. Importing to Postman:
Bring the curl command into Postman to setup the environment for further requests.
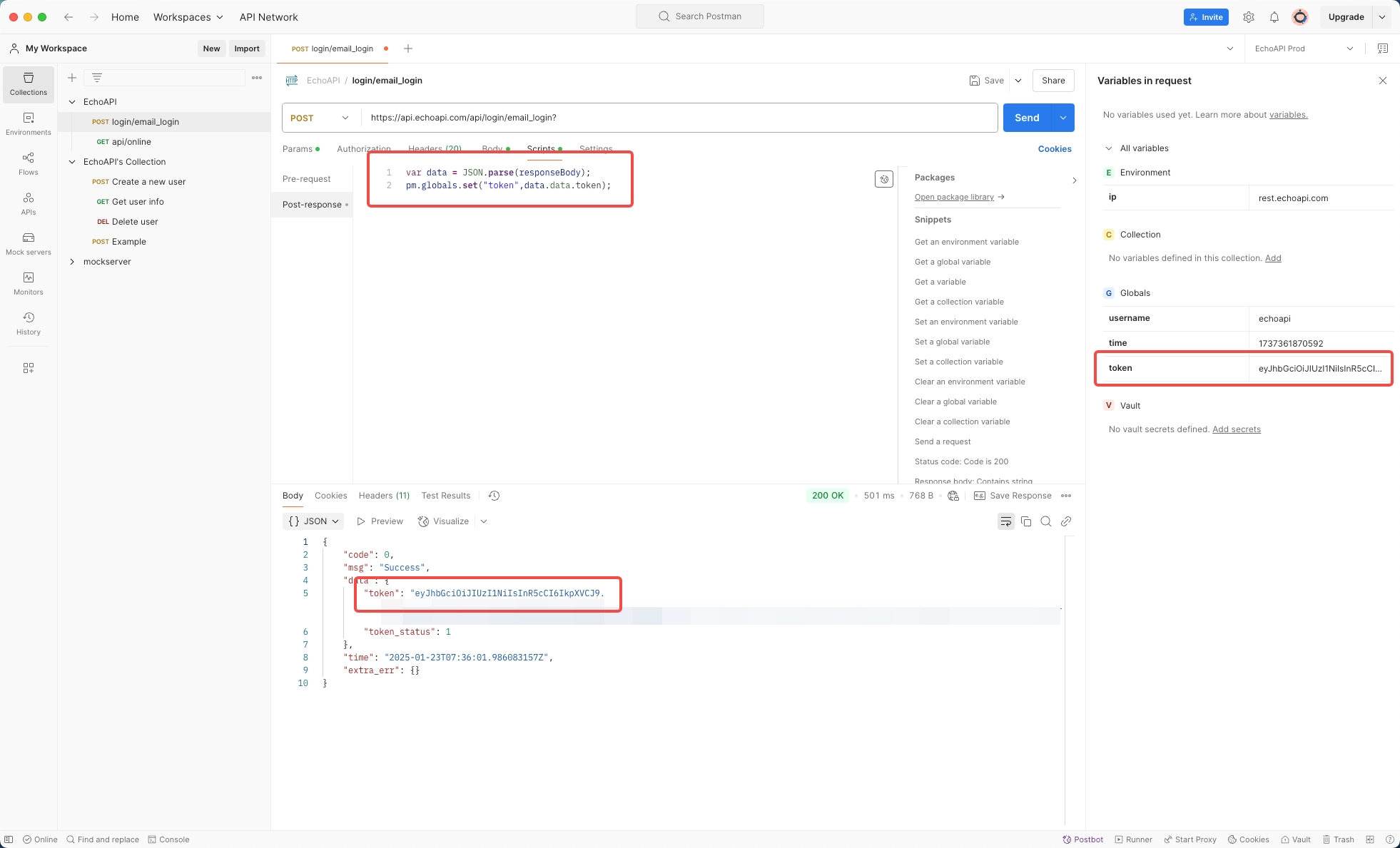
4. Token Setup in Postman:
After sending a request via the login/email_login endpoint, extract the token from the response and set it as a global variable:
var data = JSON.parse(responseBody);
pm.globals.set("token", data.data.token);

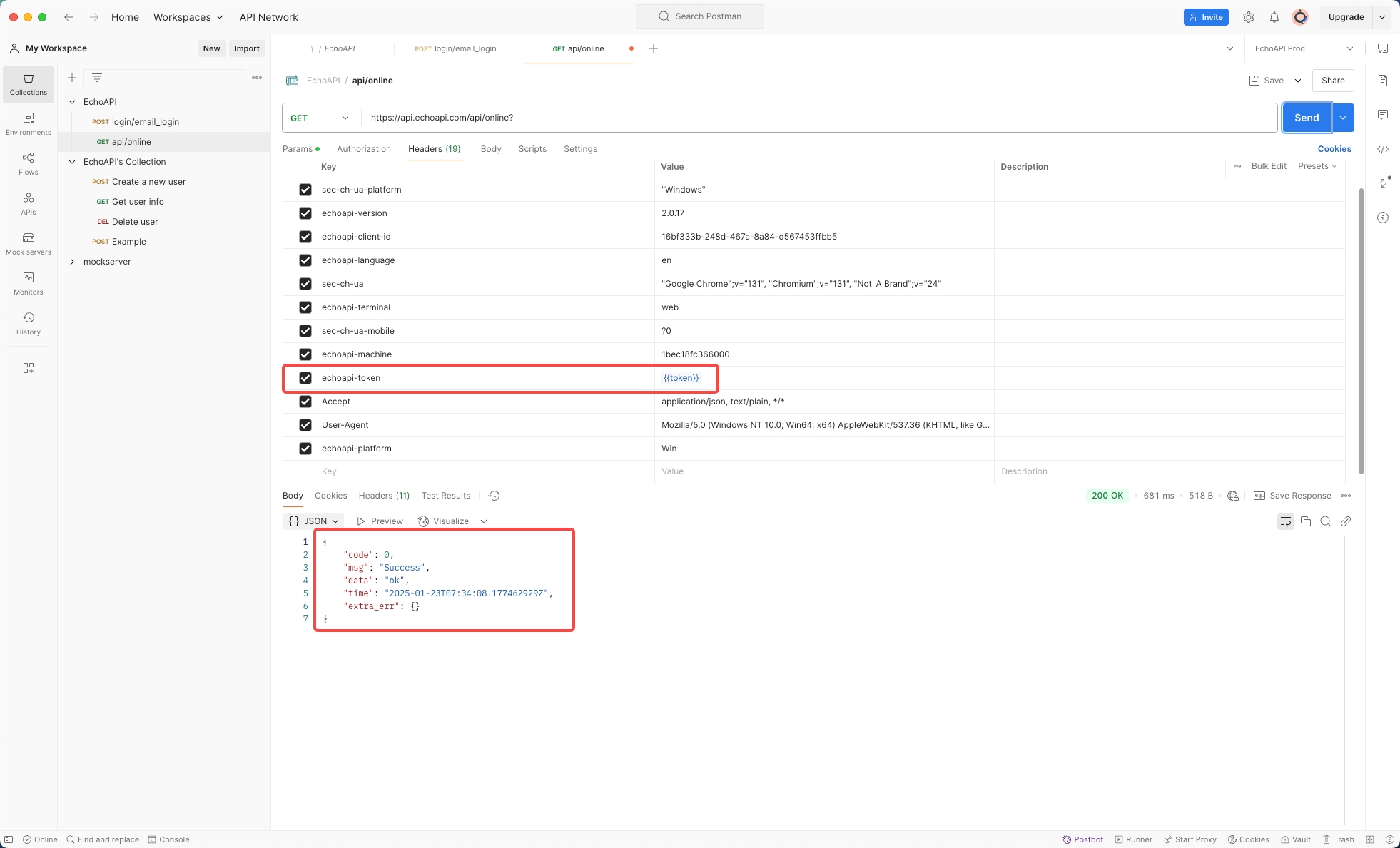
5. Using Token in Headers:
- Switch to the
api/onlineendpoint in Postman.
In the Headers section, replace the value of echoapitoken with the token variable {{token}} acquired earlier, send the request, and observe the output.
6. Attempting Cookie Authentication:
The result indicates failure, as the API requires authentication via tokens, hence validating the different authentications in use.
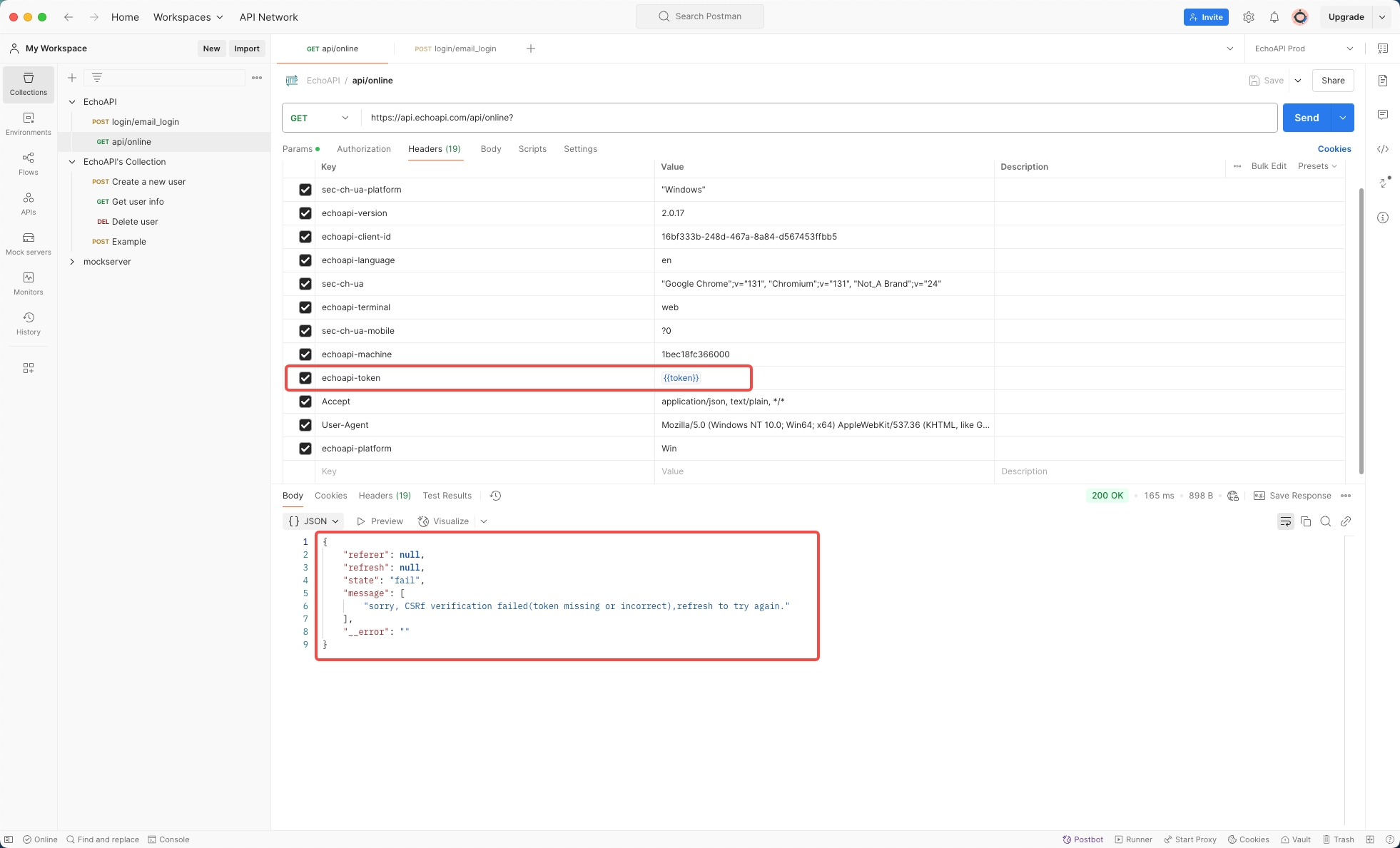
Evaluate attempting a request to api/online with all cookies deleted or disabled.
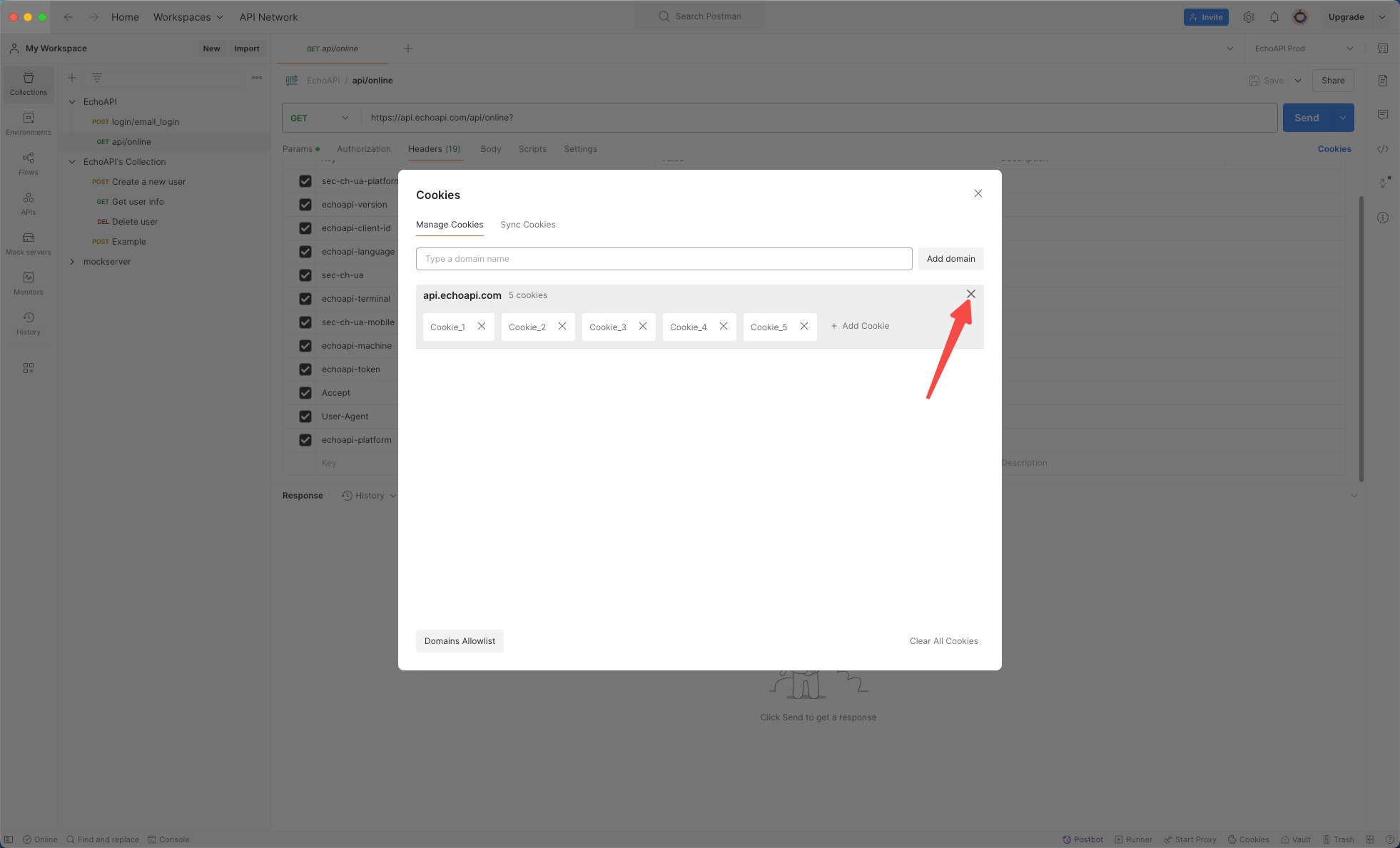

Conclusion
Through this comprehensive guide and practical example, you have learned about the mechanisms of Cookie and Token authentications, how to inspect and manipulate these using tools like Postman and echoAPI Interceptor. Cookie and Token Authentication serve different purposes and scenarios where the former manages sessions and the latter secures API calls via tokens that represent user credentials or session states.
Understanding and implementing these authentication mechanisms properly can bolster the security and functionality of web applications and services, providing a more secure and responsive user experience.




 EchoAPI for VS Code
EchoAPI for VS Code

 EchoAPI for IntelliJ IDEA
EchoAPI for IntelliJ IDEA

 EchoAPl-Interceptor
EchoAPl-Interceptor

 EchoAPl CLI
EchoAPl CLI
 EchoAPI Client
EchoAPI Client API Design
API Design
 API Debug
API Debug
 API Documentation
API Documentation
 Mock Server
Mock Server








