Understanding OAuth 1.0: A Comprehensive Overview
OAuth 1.0, short for Open Authorization 1.0, stands as a pivotal protocol in the realm of secure authorization for web applications. It serves as a robust framework enabling secure access to resources without the need to divulge user credentials. Here's a detailed exploration of OAuth 1.0 for those seeking a deeper understanding.

What is OAuth 1.0?
OAuth 1.0, the predecessor to OAuth 2.0, operates on the concept of issuing access tokens to third-party applications seeking access to user data on servers. This token-based authentication method enhances security by eliminating the need to share sensitive login information with external services.
Key Elements of OAuth 1.0
- Consumer: The entity requesting access to protected resources on behalf of the user.
- Service Provider: The server that hosts the user's resources, responsible for authenticating users and granting access.
- User: The individual who grants permission for the consumer to access their data on the service provider's platform.
- Token: A unique, temporary credential provided to the consumer after successful authentication, enabling access to the user's resources.
OAuth 1.0 Workflow
- Requesting a Request Token: The consumer initiates the process by requesting a temporary request token from the service provider.
- User Authorization: The user is directed to the service provider's authorization page to authorize the consumer's access.
- Exchanging Request Token for Access Token: After user authorization, the request token is swapped for an access token, allowing the consumer to interact with the user's resources.
- Accessing Protected Resources: With the access token, the consumer can securely access the user's data on the service provider's platform.
Benefits of OAuth 1.0
- Heightened Security: By utilizing temporary tokens, OAuth 1.0 reduces the risk associated with sharing user credentials.
- User Control: Users maintain control over which resources third-party applications can access, enhancing privacy and data security.
- Interoperability: OAuth 1.0's standardized protocol facilitates seamless integration across various platforms and services.
Challenges and Considerations
- Complexity: The OAuth 1.0 process may be intricate for developers to implement compared to newer versions like OAuth 2.0.
- Signature Requirement: OAuth 1.0 mandates the use of cryptographic signatures for requests, adding a layer of complexity to the authentication process.
Discover EchoAPI: The Comprehensive API Debugging Tool with Auth 1.0 Support
EchoAPI emerges as a game-changer in the realm of API debugging, offering a robust platform that not only streamlines the debugging process but also provides seamless support for Auth 1.0 authentication. Let's explore the features and benefits of EchoAPI in detail:
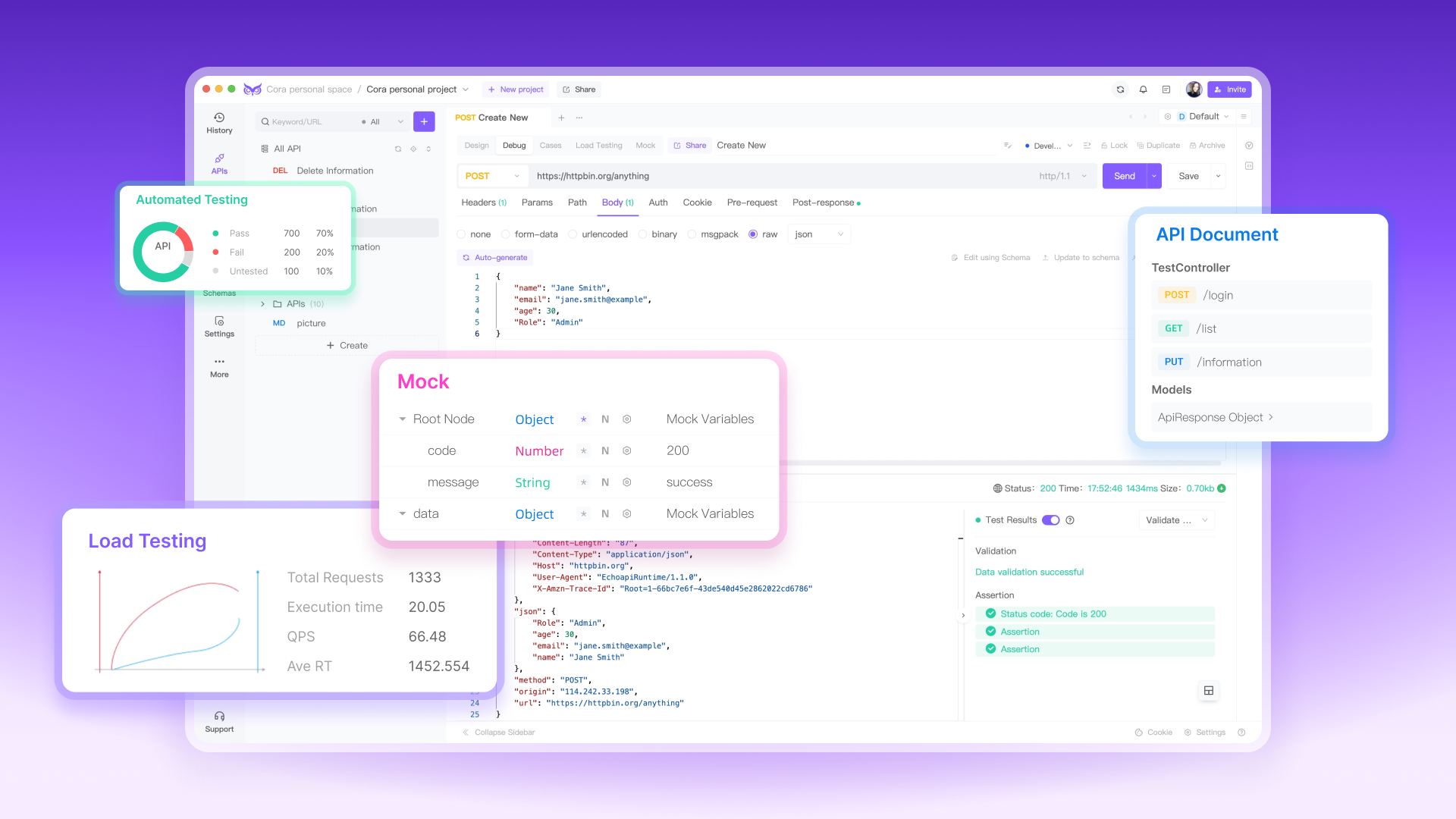
Key Features of EchoAPI
- User-Friendly Interface: EchoAPI boasts an intuitive and user-friendly interface, making API debugging a breeze for both novice and seasoned developers.
- Real-Time Monitoring: With EchoAPI, you can monitor API calls in real-time, enabling quick identification and resolution of issues as they occur.
- Customizable Requests: EchoAPI allows you to tailor API requests according to your requirements, facilitating precise testing and debugging.
- Auth 1.0 Support: One of the standout features of EchoAPI is its seamless integration with Auth 1.0 authentication, ensuring secure access to protected resources during the debugging process.
Conclusion
OAuth 1.0 serves as a foundational protocol for secure authorization, offering a robust framework for controlled access to user resources. While newer versions have gained more prominence, grasping the principles and workflow of OAuth 1.0 remains valuable for developers and security professionals alike.




 EchoAPI for VS Code
EchoAPI for VS Code

 EchoAPI for IntelliJ IDEA
EchoAPI for IntelliJ IDEA

 EchoAPl-Interceptor
EchoAPl-Interceptor

 EchoAPl CLI
EchoAPl CLI
 EchoAPI Client
EchoAPI Client API Design
API Design
 API Debug
API Debug
 API Documentation
API Documentation
 Mock Server
Mock Server








