Understanding TCP: A Fundamental Tool for Developers
By mastering TCP and utilizing advanced testing tools like EchoAPI, developers can greatly improve their network applications' effectiveness and reliability.
For developers, understanding TCP (Transmission Control Protocol) is essential. It's a core part of the Internet protocol suite that facilitates reliable communication between networked computers. This article dives into what TCP is, its key features, typical use cases, practical business examples, and how to debug TCP connections using advanced tools like EchoAPI.
What is TCP?
TCP is a connection-oriented protocol used over network-connected devices. It ensures the complete and correct delivery of data between a source and destination. TCP organizes data so that it can be transmitted between a server and client in packets, which are checked for errors upon arrival.
Key Features of TCP
TCP is renowned for its reliability and efficiency in data transmission. Here are its standout features:
- Reliable Delivery: Guarantees the delivery of data packets in the correct order without losses or duplicates.
- Error Checking and Correction: Detects errors transmitted data and prompts retransmission.
- Flow Control: Manages the pace of data transmission to prevent network congestion.
- Congestion Control: Adjusts the rate of data flow based on network traffic to minimize packet loss.
Detailed Common Use Cases for TCP
Transmission Control Protocol (TCP) is pivotal in a multitude of applications across various industries due to its reliable data transmission capabilities. Here's a more detailed look at some of the significant scenarios where TCP is typically employed:
- Web Browsing:
Most of the web’s content is delivered via HTTPS, which utilizes TCP at its core. TCP ensures that web pages (HTML, CSS, JavaScript, and media files) are transmitted from the server to your browser reliably and in order. Websites where transaction integrity is crucial, like online banking, e-commerce sites, and government portals, particularly rely on TCP's robustness. - Email Services:
Email protocols such as SMTP (Simple Mail Transfer Protocol) for sending emails, as well as POP (Post Office Protocol) and IMAP (Internet Message Access Protocol) for retrieving emails, all use TCP. This ensures that all messages are sent and received without corruption, a crucial aspect given the importance of email communications in business and personal contexts. - File Transfers:
Protocols like FTP (File Transfer Protocol) and SFTP (SSH File Transfer Protocol) rely on TCP to manage the transmission of files across the internet and within local networks. TCP’s ability to manage large data transfers efficiently, check for errors, and confirm file integrity makes it ideal for these applications. - VPN Connections:
VPNs (Virtual Private Networks) often use TCP to secure and encapsulate data traffic over the internet. TCP’s inherent error-checking and recovery abilities ensure that data integrity and transmission security are maintained, which is vital for remote access and privacy protection. - Database Management Systems:
Many remote database access systems utilize TCP to ensure reliable transaction handling and data retrieval. For example, Microsoft SQL Server and MySQL, widely used in enterprise environments, support client-server communication over TCP. - Streaming Services:
While many modern streaming technologies are moving towards using UDP (User Datagram Protocol), TCP is still extensively used, particularly where playback continuity and order are more critical than real-time performance, such as in progressive downloading and some types of live streaming where reliability is more crucial than latency. - Real-Time Data Processing:
In financial services, such as stock trading platforms or banking systems, TCP is used for transmitting real-time data and executing transactions. The reliability of TCP ensures that stock trades and financial transactions are executed timely and error-free, which are essential for maintaining financial integrity and compliance.
Each use case benefits significantly from TCP's features such as reliable data transfer, ordered packets, error detection, and congestion control. These features are crucial for maintaining the integrity and security of data in scenarios where errors or data loss could result in significant issues or costs. Hence, TCP's widespread adoption in areas requiring high reliability shows its unmatched utility in network communications.
A Practical Example of TCP in Business
Consider a financial services company that uses a TCP-based application for real-time transaction processing. The company benefits as follows:
- Reliability: Ensures all transactions are processed accurately.
- Security: TCP's built-in error checking aids in preventing data tampering and corruption.
- Performance: Fast, ordered data delivery is critical in transactions.
A typical TCP implementation might involve setting up a secure, fault-tolerant server environment that handles thousands of simultaneous connections. Here’s a simple example of a server setup code:
import socket
s = socket.socket(socket.AF_INET, socket.SOCK_STREAM)
s.bind(('localhost', 9999))
s.listen(5)
print('Server listening on localhost:9999')
while True:
client_socket, addr = s.accept()
print('Connected by', addr)
while True:
data = client_socket.recv(1024)
if not data:
break
client_socket.sendall(data)
client_socket.close()
Debugging TCP with EchoAPI
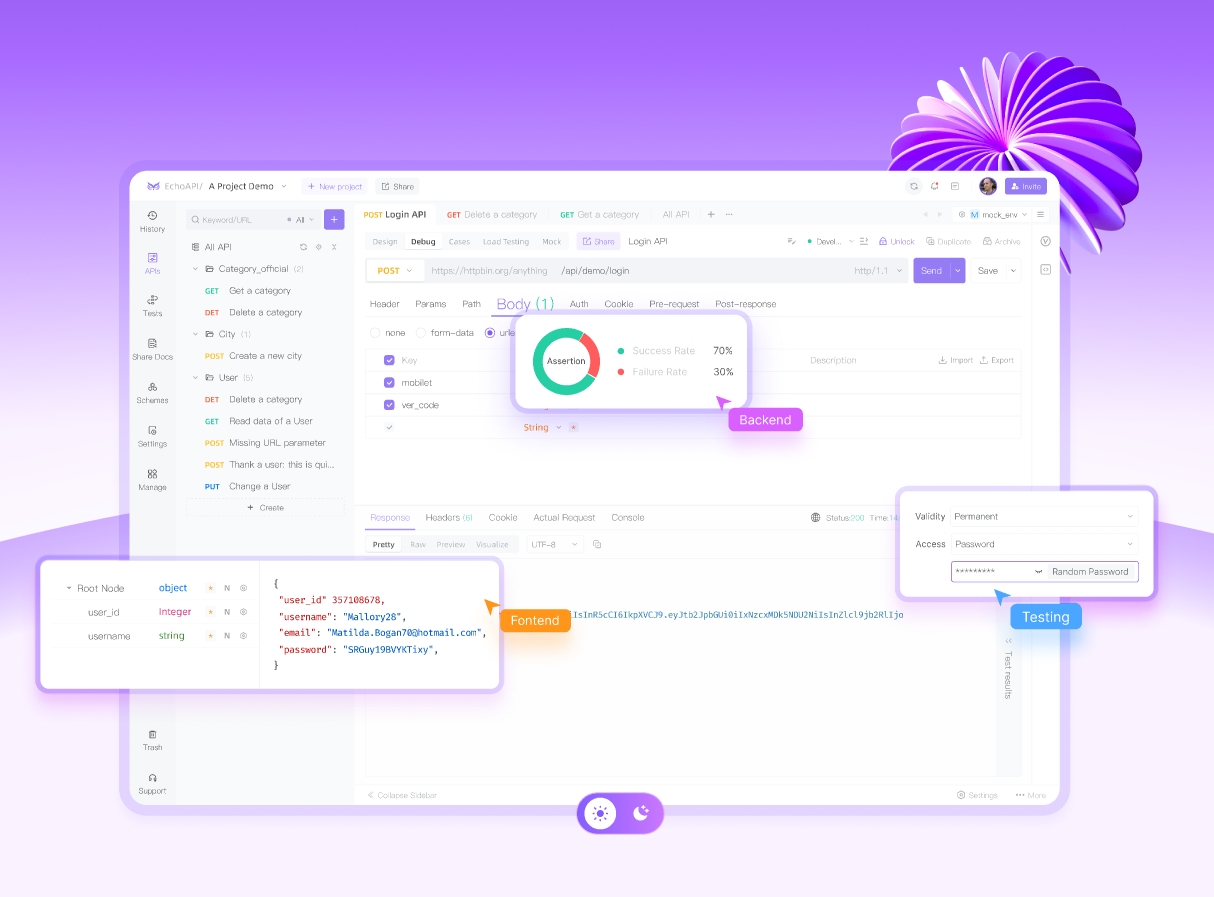
EchoAPI is a versatile debugging tool that supports various protocols including HTTP, WebSocket, TCP, SSE, and GraphQL. To debug a TCP connection using EchoAPI, developers can simulate TCP requests to their server and analyze responses. This helps in validating flow control, error handling, and the overall resilience of the TCP application.
Create a New TCP Method
In the directory sidebar, select "More Operations" and then "Create New TCP Method."
Basic Information
:::caution
The TCP method’s service address is inherited from the parent client and cannot be modified directly. Changes must be made at the client level.
:::
The Debug page also supports adding detailed descriptions of the interface.
Request Message
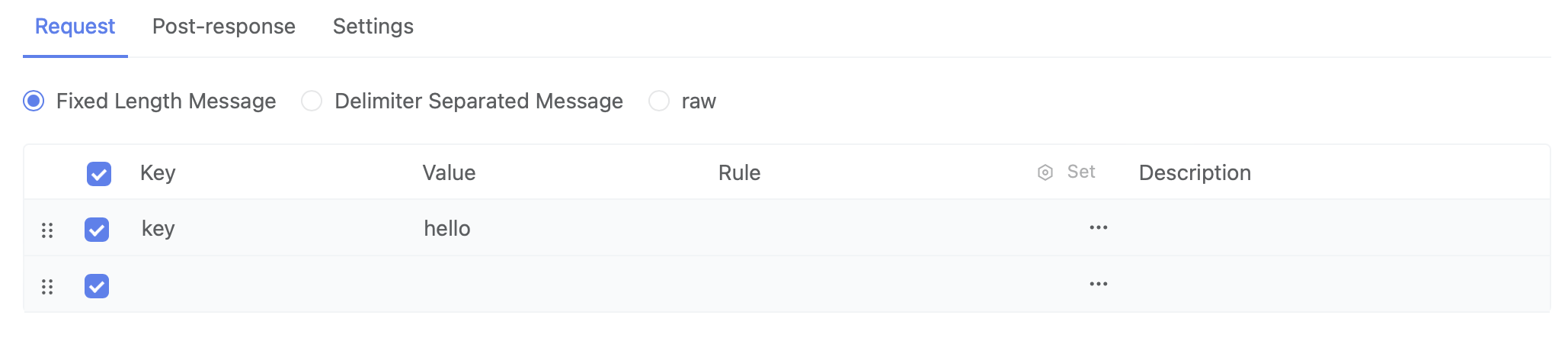
Supports fixed-length message, separator message, and raw (xml/json/text/) format request messages.
Fixed-Length Message
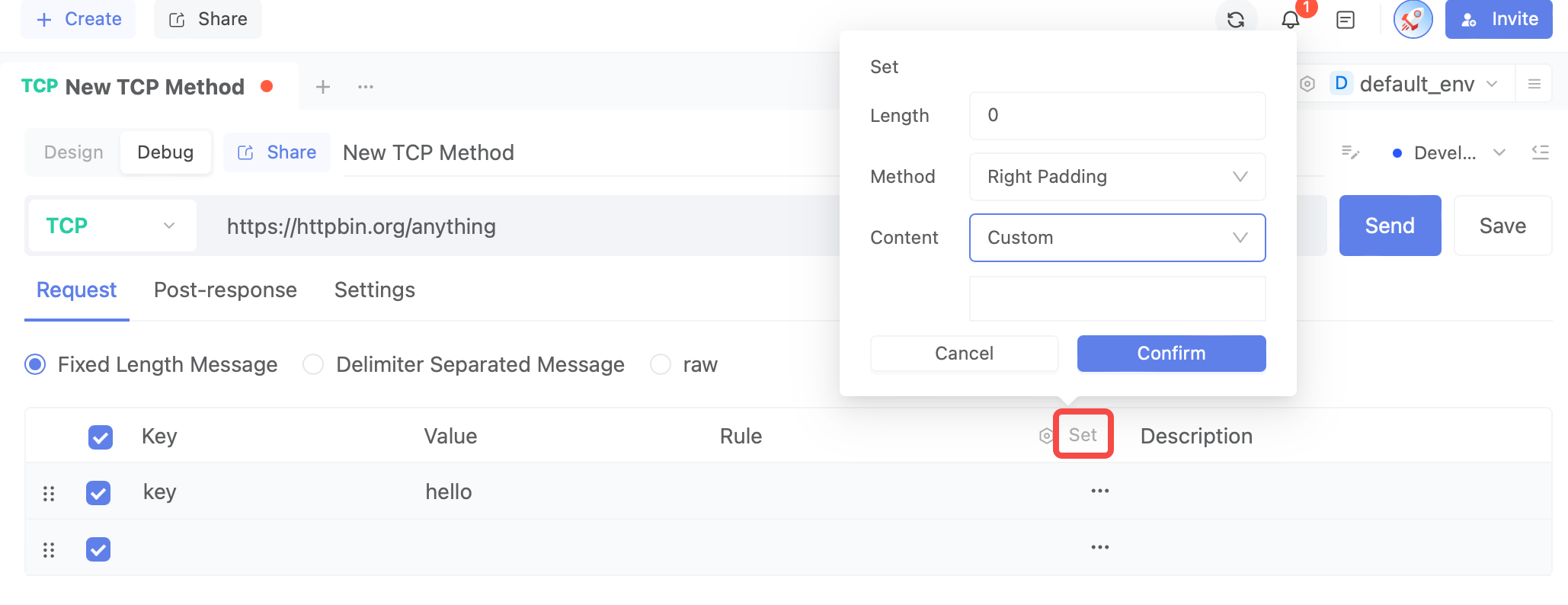
If the length is insufficient, you can set padding rules.
How to Set Padding Rules
Separator Message
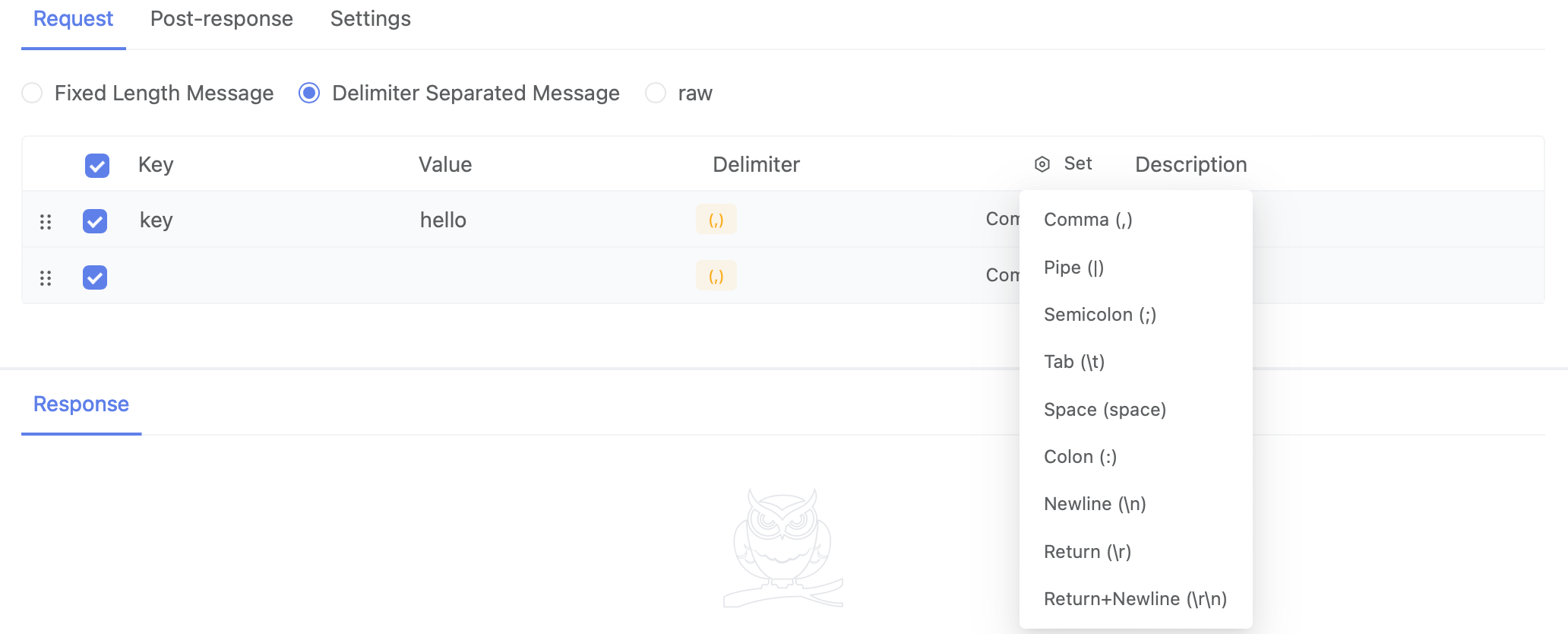
Supports setting a separator between each parameter value in the message.
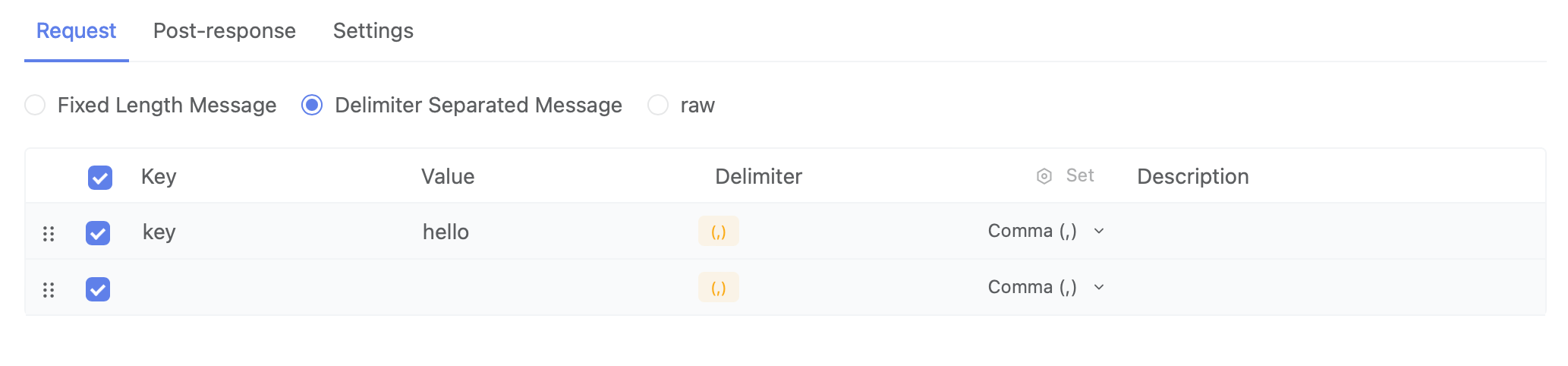
How to Set Separator Rules
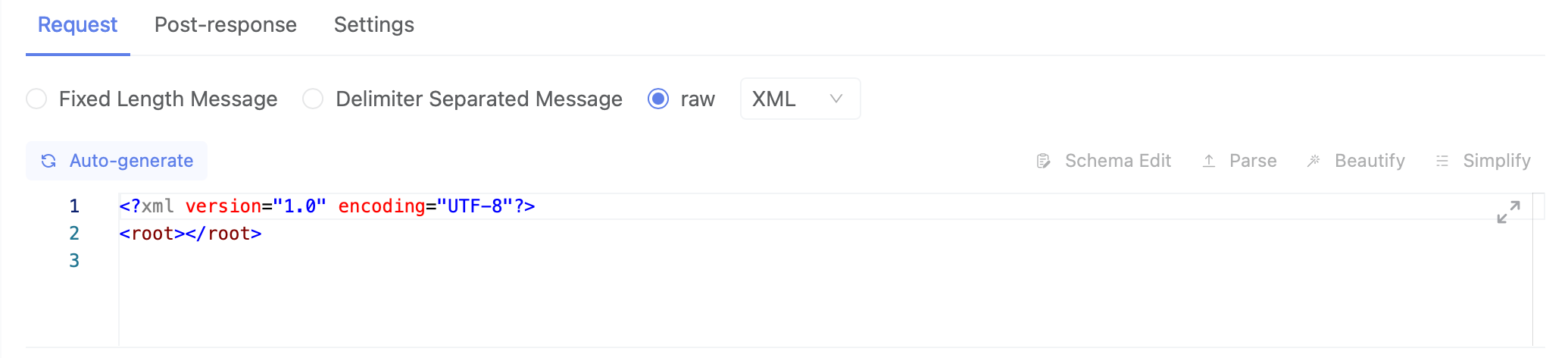
Raw
When sending JSON, XML, or text formats, switch to the corresponding raw type.
Raw (json/xml):
Supports visual editing for designing request messages with hierarchical JSON or XML structures.
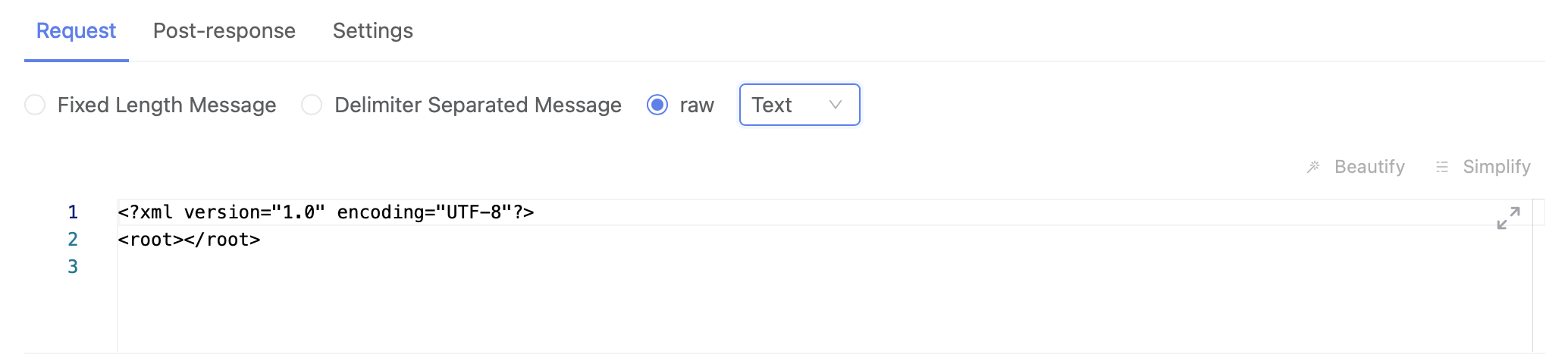
Raw (Text): Supports source code editing for designing the parameter values of input parameters.
Post-response Operations
You can add assertions in post-response operations to verify the TCP response message with assertions. Click to learn about the use of assertions.
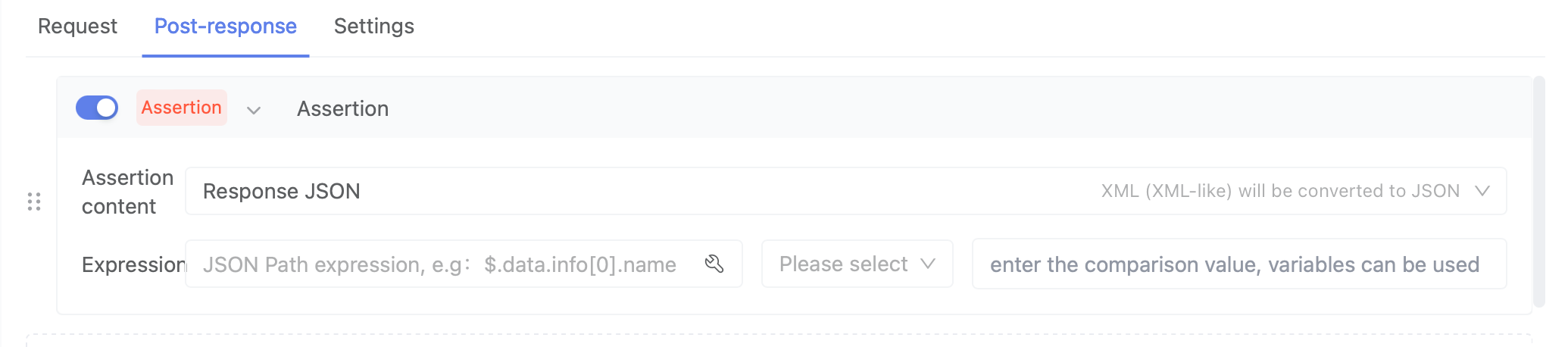
Settings
You can configure the request message encoding format, request data processing function, and the return data processing function under the settings tab.
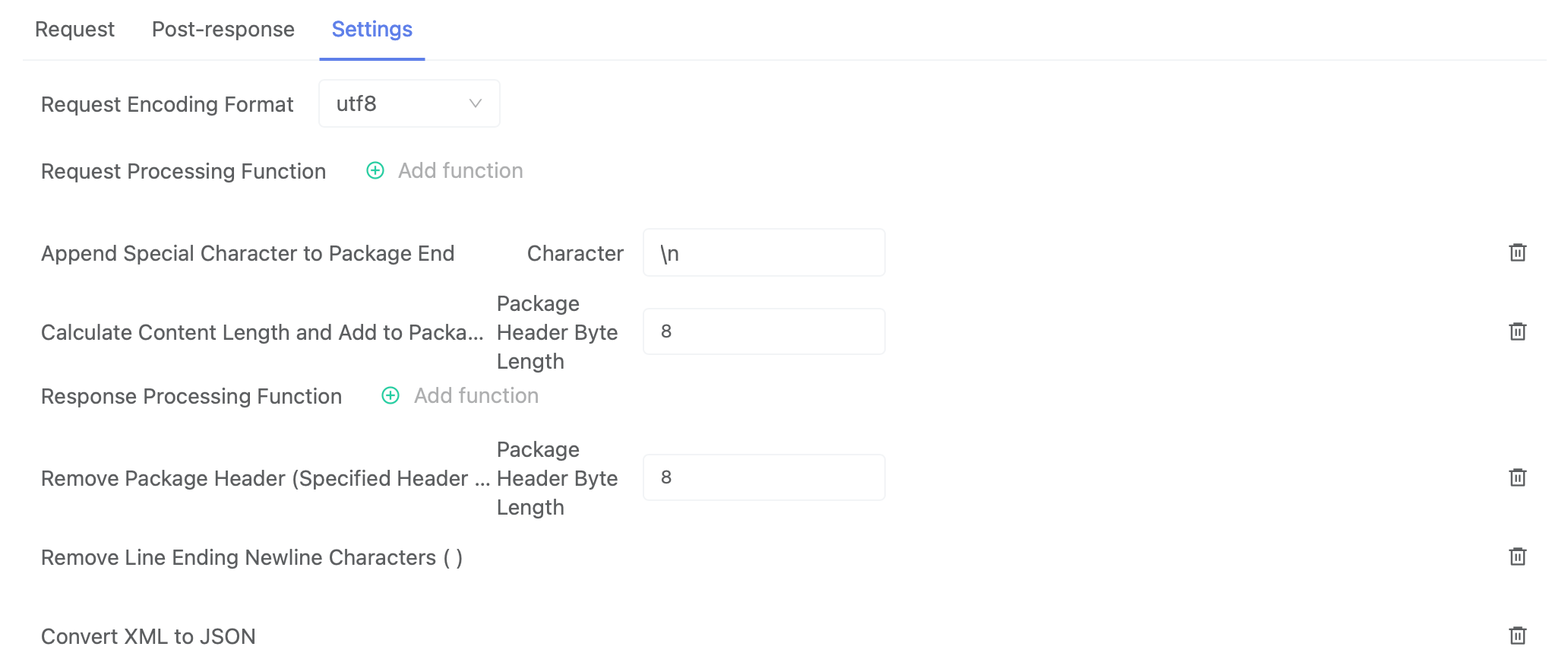
Response Area
The Necessity of TCP
TCP plays a pivotal role in ensuring that essential and sensitive data is exchanged reliably and securely across the internet. Its design is crafted to navigate the unpredictable nature of network communications, making it indispensable for maintaining data integrity.
Conclusion
Understanding TCP thoroughly is crucial for any developer working with internet and network applications. Tools like EchoAPI enhance one’s ability to test and ensure the robustness of applications that use TCP. Given TCP's role in the foundational aspects of the internet, mastering it is not just necessary, but mandatory for creating sophisticated, reliable network applications.
In conclusion, TCP's relevance remains unquestioned in the landscape of internet communication, asserting its position as a critical element of network-related development. By mastering TCP and utilizing advanced testing tools like EchoAPI, developers can greatly improve their network applications' effectiveness and reliability.




 EchoAPI for VS Code
EchoAPI for VS Code

 EchoAPI for IntelliJ IDEA
EchoAPI for IntelliJ IDEA

 EchoAPl-Interceptor
EchoAPl-Interceptor

 EchoAPl CLI
EchoAPl CLI
 EchoAPI Client
EchoAPI Client API Design
API Design
 API Debug
API Debug
 API Documentation
API Documentation
 Mock Server
Mock Server








