What's the difference between HTTP and HTTPS? How to debug HTTPS REST API?
EchoAPI supports debugging and stress testing for HTTP REST APIs, and it doesn't stop there. It also handles HTTPS REST APIs, TCP, and SSE (Server-Sent Events).
HTTP Data Transmission
HTTP: The HyperText Transfer Protocol
HTTP, short for HyperText Transfer Protocol, defines the standards for client requests and server responses. Essentially, it uses TCP as the underlying method for data transmission.
When a user sends a request, it goes through a TCP three-way handshake, allowing the data to be transmitted to the server and waiting for the server's response. However, this round-trip transmission is in plaintext. If a malicious eavesdropper intercepts the communication, the data could be exposed or misused. 😱
You think no one would bother? Many do! For instance, malicious users might set up fake public Wi-Fi to intercept packets and spy on transmitted data. Even if you avoid unknown free Wi-Fi, you can’t verify that every node in your network path to the server is secure and not intercepting your data.
Transmitting unencrypted data is like running naked on the internet. To avoid such risks, we need to encrypt the data.
Encryption
Encryption is the process of converting plaintext data into unreadable content—ciphertext, which can only be converted back to plaintext through a specific decryption process. 🔐
Symmetric Key Encryption
For example, consider the famous Caesar cipher: a basic method where letters in plaintext are shifted by a set distance. To decrypt, simply shift them back. If “EGG” is the plaintext and the key is 3, the ciphertext would be “HJJ”.
Of course, real-world encryption uses more sophisticated methods like AES. Both symmetric key encryption and AES use the same key for encryption and decryption, hence the term "symmetric key encryption."
Is symmetric key encryption secure? Not entirely. Imagine if two people need to share a key before they can communicate securely. The key transmission itself might be intercepted, compromising security.
Asymmetric Key Encryption
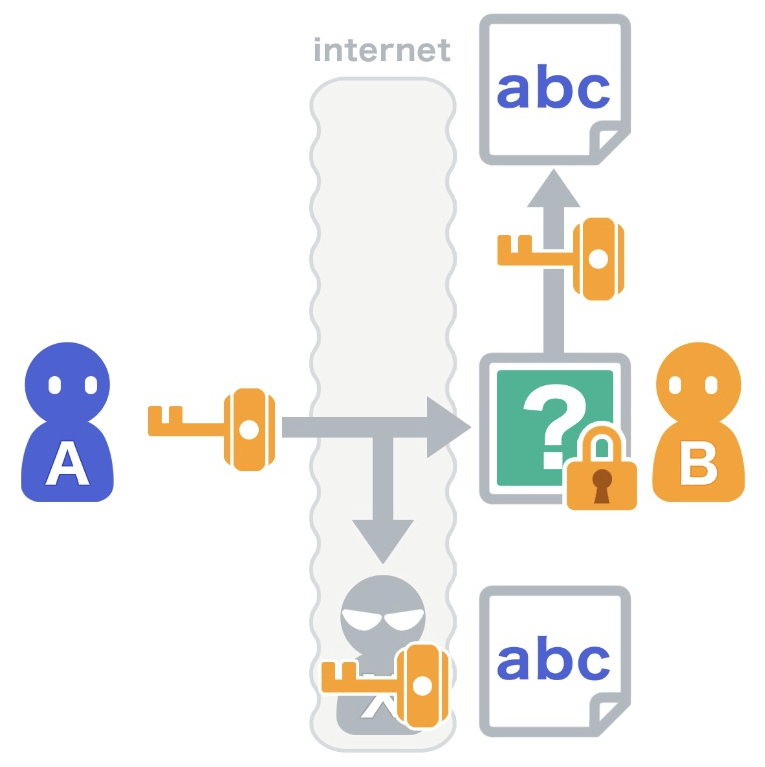
This brings us to asymmetric key encryption, also known as public key encryption. Here, each participant has a pair of keys: a public key available to everyone and a private key kept secret. Data encrypted with one key can only be decrypted by its paired key.
Imagine Alice and Bob want to communicate while Eve is eavesdropping. Alice encrypts her message with Bob’s public key. Only Bob can decrypt it with his private key, even if Eve intercepts it.
Can we now communicate without worry? Not entirely. While participants see each other's public keys, they can’t verify the ownership. 🧐

Digital Certificates
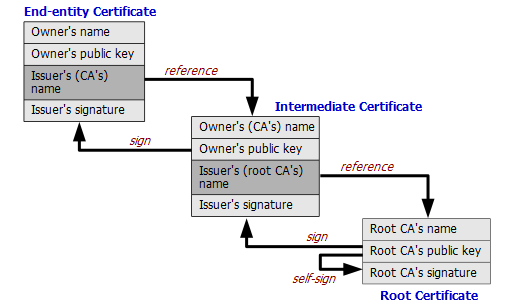
Enter Certification Authorities (CAs). Before Alice and Bob communicate, Alice provides her public key and email to a CA, which issues a digital certificate after verification.
Digital certificates ensure that public keys belong to their respective owners, preventing man-in-the-middle attacks. When communication starts, Alice sends her certificate to Bob, who verifies it through the CA’s digital signature.
But with so many websites, how do we manage all these certificates? CAs form a trust chain, where a root CA vouches for intermediate CAs, which in turn vouch for end-user certificates.
What is HTTPS?
HTTPS, short for HyperText Transfer Protocol Secure, incorporates SSL/TLS to encrypt HTTP communications, providing a secure data transmission method. 🌐
Due to the computational intensity of asymmetric encryption, HTTPS uses it primarily to exchange symmetric keys, subsequently using them for faster data encryption.
The Impact of HTTPS on Websites
- Enhanced Security: HTTPS ensures data between the server and browser remains encrypted, crucial when handling sensitive information like passwords and credit card details.
- SEO Boost: Google considers HTTPS a ranking signal, potentially leading to better search results for secure websites.
- Increased User Trust: Browsers show a secure lock icon for HTTPS sites, boosting user confidence in making transactions.
Migrating from HTTP to HTTPS
- Obtain an SSL Certificate: Purchase from a provider or use a free service like Let’s Encrypt.
- Install and Configure SSL Certificate: Depending on your hosting provider and server software, this process may vary.
- Update Website Links to HTTPS: Change all internal resources to use HTTPS. Some CMS platforms have plugins to automate this.
- Set up 301 Redirects: Ensure browsers automatically redirect HTTP requests to HTTPS, beneficial for both user experience and SEO.
- Update URLs in Google Search Console and Analytics: Maintain traffic and SEO data by updating your URLs.
- Test: Use various tools to ensure all content loads correctly and HTTPS is properly set up.
How to debug HTTPS REST API?
EchoAPI is a robust REST API debugging tool. It supports not only HTTP REST APIs but also HTTPS REST APIs, TCP, SSE (Server-Sent Events), and more. From debugging to stress testing, it’s a highly popular tool among developers.
Step ⒈ Open EchoAPI and create a new request.
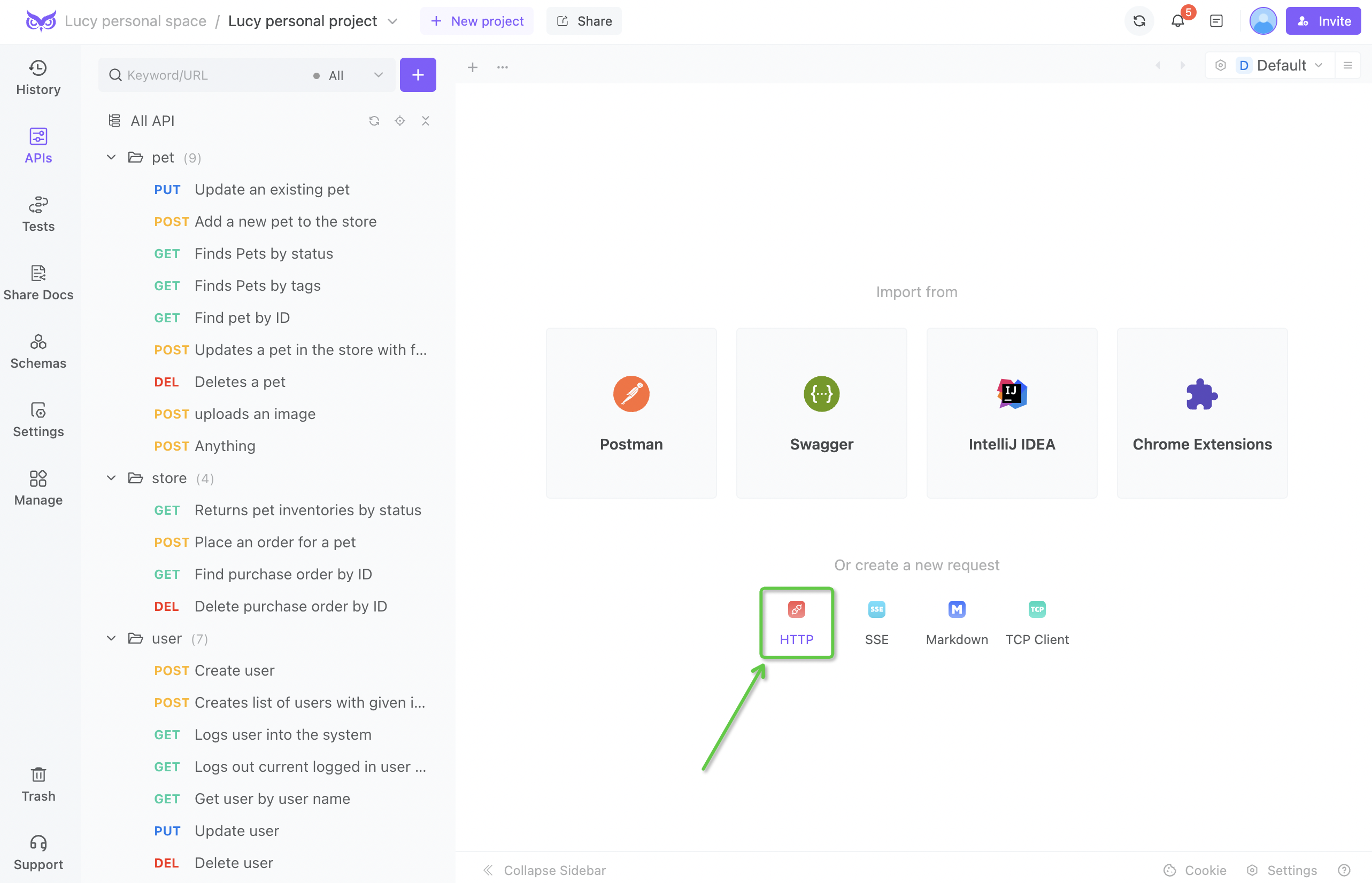
Step 2. Input an API URL starting with https:// and the request parameters.
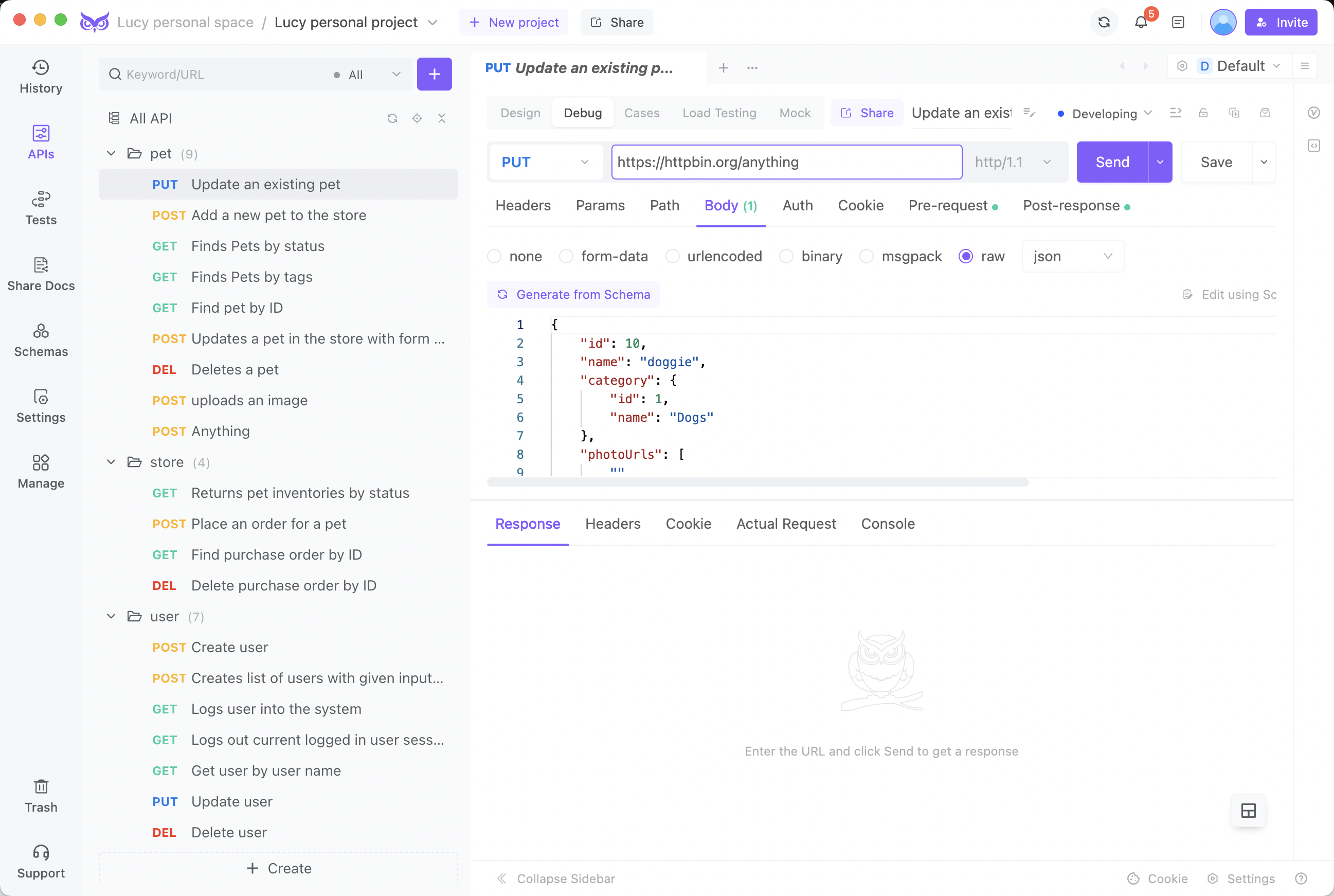
Step 3. If needed, configure the appropriate certificates
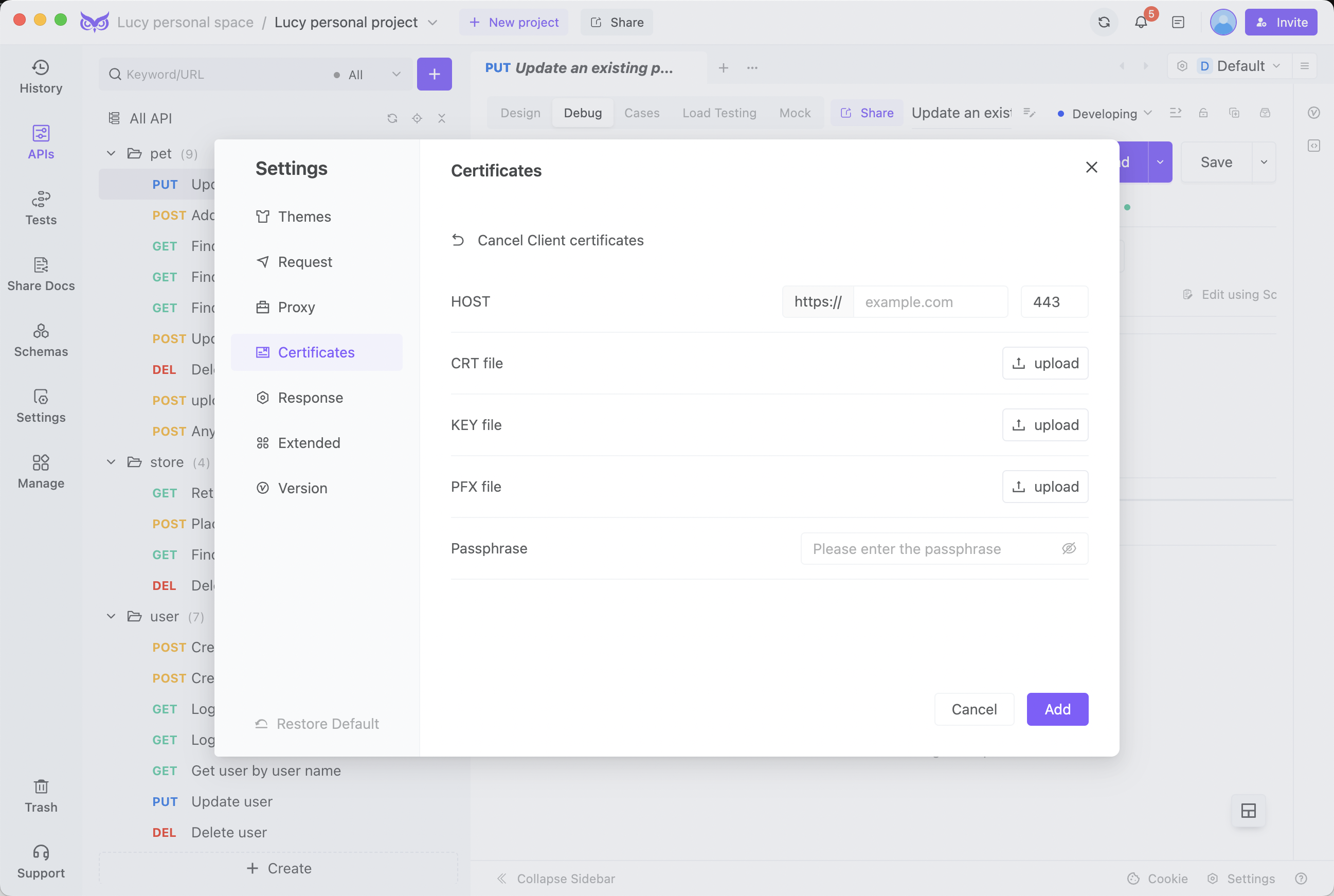
After completing the steps above, just hit the "Send" button.
Conclusion
We’ve explored encryption methods to counter threats and gradually evolved to today’s prevalent encryption techniques, highlighting the distinctions between HTTP and HTTPS. Hopefully, this overview provides a foundational understanding of internet communication security. 🌍💬




 EchoAPI for VS Code
EchoAPI for VS Code

 EchoAPI for IntelliJ IDEA
EchoAPI for IntelliJ IDEA

 EchoAPl-Interceptor
EchoAPl-Interceptor

 EchoAPl CLI
EchoAPl CLI
 EchoAPI Client
EchoAPI Client API Design
API Design
 API Debug
API Debug
 API Documentation
API Documentation
 Mock Server
Mock Server








